Enauthorization To Operate Template - DHS Security Authorization Templates This page contains templates that are used in the Security Authorization process for the Department of Homeland Security s sensitive systems Attachment Attachment column arrow image representing sort order up is ascending down is descending and up down is unsorted Ext
With the right template you can create a professional legally binding letter of authorization that clearly outlines the scope of the power you re granting In this blog post we ll provide you with five ready to use templates for your letter of authorization 1 Authorization Letter Template to Act as Representative
Enauthorization To Operate Template

Enauthorization To Operate Template
Authorization letter from a property owner. A property owner writes this letter to grant the named party permission to undertake specified actions within the premises. Such actions may include modifying, repairing, and maintenance of the property. Samples: Sample: Authorization Letter to Sell Property. Template: Authorization Letter to Sell ...
To use our Letter of Authorization template follow these steps Customize the letter with your information Sign the letter Give a copy to the authorized person Keep a copy for your records Stay in communication with the authorized person to ensure that they understand their responsibilities and carry out the tasks or actions as intended
5 Ready To Use Templates For Letter Of Authorization
A letter of authorization template is a record of permitting a person or recipient to carry out a particular task that may not be necessary for daily life any vital task Authorization and permissions can only be granted by a person of a certain standard that is qualified enough to issue You may also like Rent Increase Letter Template

Global Operate Campaign Move Beyond Conventional Outsourcing Model
ATO stands for authorization to operate also known as authority to operate Because there is no perfect risk free software system the ATO process is aimed at minimizing and managing risk responsibility This process mostly comes from the Federal Information Security Management Act FISMA legislation FISMA was an effort to

Work Authorization Form Example Sample Templates Sample Templates
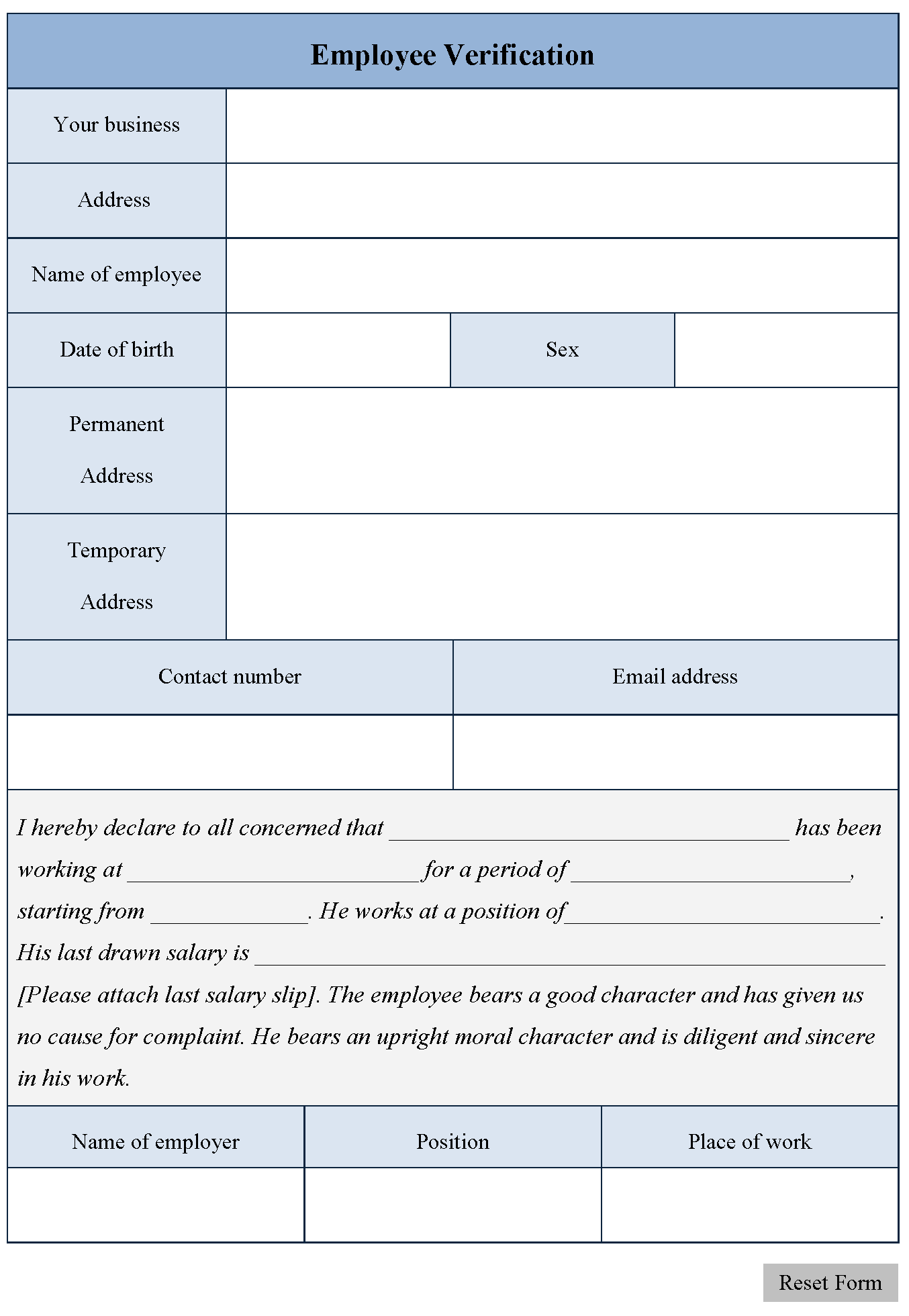
Employee Verification Form Editable PDF Forms
DHS Security Authorization Templates Homeland Security
Pursuing a FedRAMP Agency Authorization There are two approaches to obtaining a FedRAMP Authorization a provisional authorization through the Joint Authorization Board JAB or an authorization through an agency In the Agency Authorization path agencies may work directly with a Cloud Service Provider CSP for authorization at any time

Freedom To Operate FTO Analysis Sample Report Sagacious IP
This PDF document provides answers to frequently asked questions about the authorize step of the NIST Risk Management Framework a six step process for managing cybersecurity and privacy risks in information systems and organizations The document explains the purpose scope roles and activities of the authorize step as well as how to use the NIST security and privacy control baselines and
The required steps for conducting the ATO security authorization process are: Categorize the information systems in the organization, i.e., determine the criticality of the information system based on potential adverse impact to the business. Select baseline security controls.
52 Best Authorization Letter Samples Free Templates
Use this parental consent form to collect written approval from parents with regards to their children engaging in certain activities such as field trips or sports This form template serves as a formal authorization from the parent or guardian and it helps to prevent any legal implications that can arise in the future
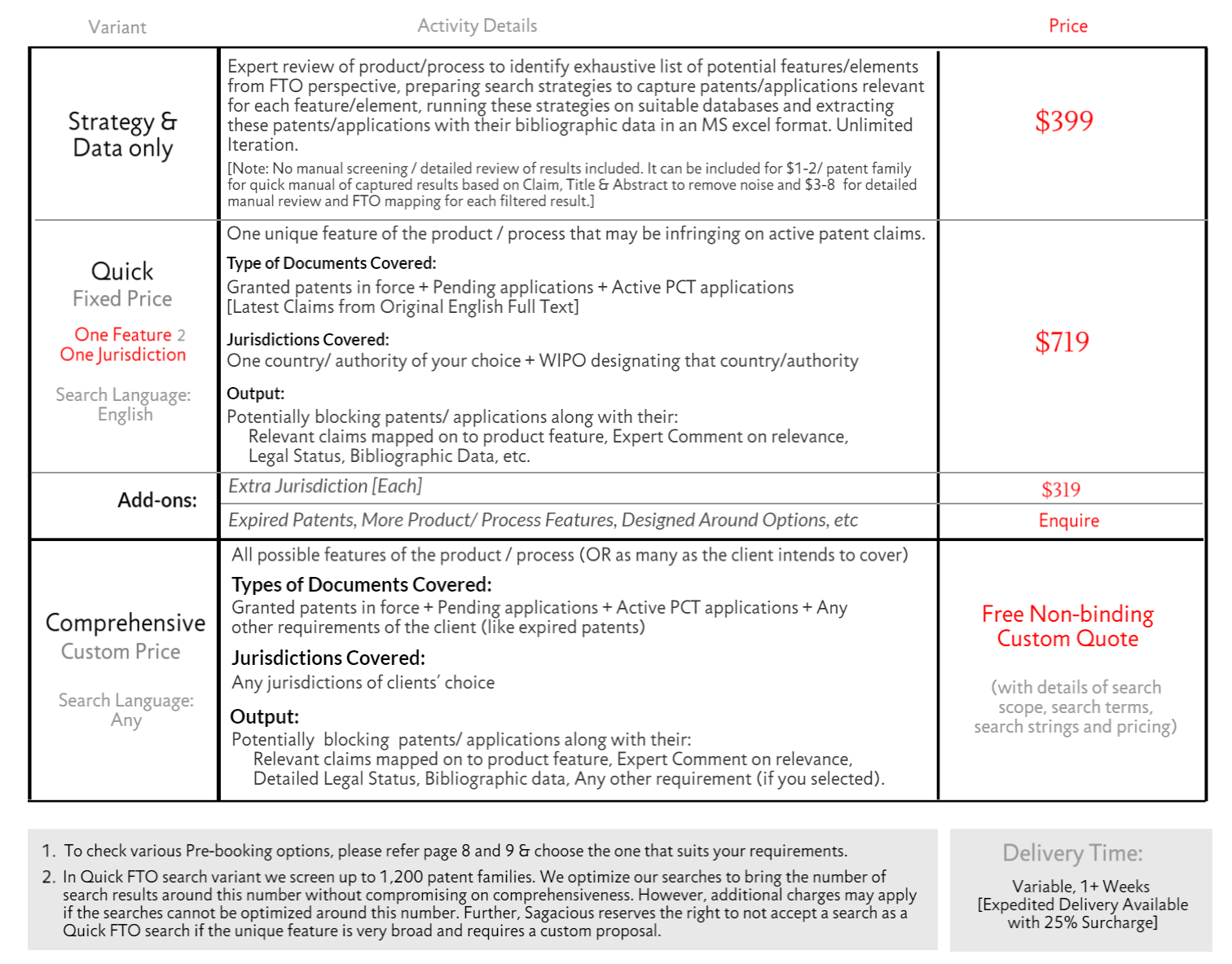
Freedom To Operate FTO Search The Patent Search Firm

Authorization To Operate Template
Enauthorization To Operate Template
This PDF document provides answers to frequently asked questions about the authorize step of the NIST Risk Management Framework a six step process for managing cybersecurity and privacy risks in information systems and organizations The document explains the purpose scope roles and activities of the authorize step as well as how to use the NIST security and privacy control baselines and
With the right template you can create a professional legally binding letter of authorization that clearly outlines the scope of the power you re granting In this blog post we ll provide you with five ready to use templates for your letter of authorization 1 Authorization Letter Template to Act as Representative

Freedom To Operate FTO Analysis Sample Report Sagacious IP

Design Build Proposal

Should Contractors Operate Separate Entities Florio Perrucci Steinhardt Cappelli Tipton

Boston Scientific Neuromodulation SC 5200 SCS Implant System Handheld Programmer User Manual FCC

Operators Operate First