Eninformation Security Policy Template For Startups - This is largely due to financial reasons as startups are far less likely to have the capital needed to implement robust information security management programs Moreover often times startups neglect to place an emphasis on information security from the start because of a lack of understanding of the threats their industry is faced with
Cisecurityms isac NIST Function Identify Page 3 ID SC 4 Suppliers and third party partners are routinely assessed using audits test results or other forms of evaluations to confirm they are meeting their contractual
Eninformation Security Policy Template For Startups

Eninformation Security Policy Template For Startups
Get ahead of your 2023 security goals. Download our information and cyber security policy templates for SMBs, startups, and enterprises.
Adapt existing security policies to maintain policy structure and format and incorporate relevant components to address information security Establish a project plan to develop and approve the policy Create a team to develop the policy Schedule management briefings during the writing cycle to ensure relevant issues are addressed
Span Class Result Type
An information security policy can be tough to build from scratch it needs to be robust and secure your organization from all ends It should cover all software hardware physical parameters human resources information and access control It also needs to be flexible and have room for revision and updating and most importantly it needs
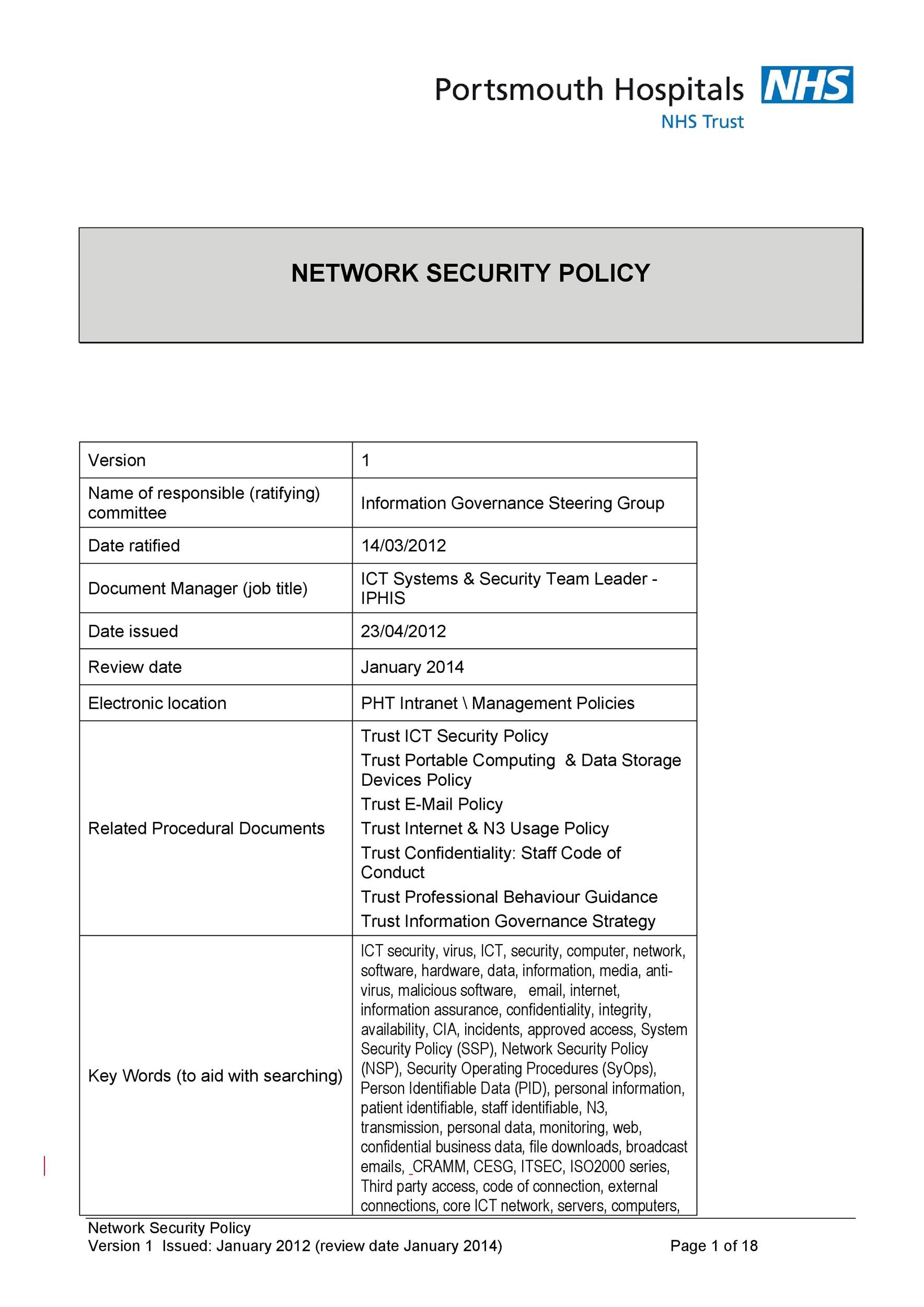
Security Policy Template Free Database
Larger companies have employees sign an information security policy It s one of those things you have to eventually do for compliance reasons After checking a compliance box they are largely

New Physical Security Policy Template Policy Template Letter

42 Information Security Policy Templates Cyber Security TemplateLab
Quickstart To Information Security Policies For Startups
Data backup Encrypt data backup according to industry best practices both in motion and at rest Securely store backup media or move backup to secure cloud storage Movement of data Only transfer data via secure protocols Encrypt any information copied to portable devices or transmitted across a public network

Free IT Security Policy Template A Step By Step Guide
1 Purpose and Scope The objective of this Information Security Policy is to set the high level policies and principles for information security in our organisation This policy applies to all
Investing in the development and enforcement of an information security policy is well worth the effort. There are many components of an information security policy. Fundamental elements include: Information security roles and responsibilities. Minimum security controls. Repercussions for breaking information security policy rules.
Information Cyber Security Policy Templates PurpleSec
Whether you need a starting point for developing your first information security policy or would like to use our template to benchmark your own policy download this sample policy template from top law firm Baker McKenzie and put it to work for you today For anyone responsible for Writing and disseminating IT security policies to employees

42 Information Security Policy Templates Cyber Security TemplateLab

Free IT Security Policy Template A Step By Step Guide
Eninformation Security Policy Template For Startups
1 Purpose and Scope The objective of this Information Security Policy is to set the high level policies and principles for information security in our organisation This policy applies to all
Cisecurityms isac NIST Function Identify Page 3 ID SC 4 Suppliers and third party partners are routinely assessed using audits test results or other forms of evaluations to confirm they are meeting their contractual
Policy Template Clinical Policy Monofilament Testing

Classles Democracy Policy And Procedure Manual Template

Physical Security Policy And Procedures Template Database

ISMS Policy Template ISO27001 ISMS Information Security Policy Word

42 Information Security Policy Templates Cyber Security TemplateLab