Eninsider Threat Plan Template - The Intelligence Community Equal Employment Opportunity and Diversity EEOD Office is responsible for the overall management of the ODNI EEO and Diversity Program and provides IC wide oversight and guidance in developing implementing and measuring progress in EEO diversity and inclusion
An insider threat is a security risk that originates from within the targeted organization It typically involves a current or former employee or business associate who has access to sensitive information or privileged accounts within the network of an organization and who misuses the access
Eninsider Threat Plan Template

Eninsider Threat Plan Template
Assistant Director America's critical infrastructure assets, systems, and networks, regardless of size or function, are susceptible . to disruption or harm by an insider, or someone with institutional knowledge and current or prior authorized
Establishing a Foundation and Building an Insider Threat Program Establishing a brand new process function or program can be daunting Some of the challenges include determining where to start researching whether it has been done successfully in the past and if it has discovering the best practices and frameworks that can be used as a
Span Class Result Type
Center f or Development of S ecurit y Ex cellence MAY 2022 JOB AID INSIDER THREAT PROGRAM ITP FOR INDUSTRY

Threat Assessment Report Template
Insider Threat Programs are designed to deter detect and mitigate actions by insiders who represent a threat to national security If you are new to Insider Threat Program Management or Operations we recommend you review the training products in the order listed to develop a foundation in Insider Threat Program Management and Operations concepts and principles
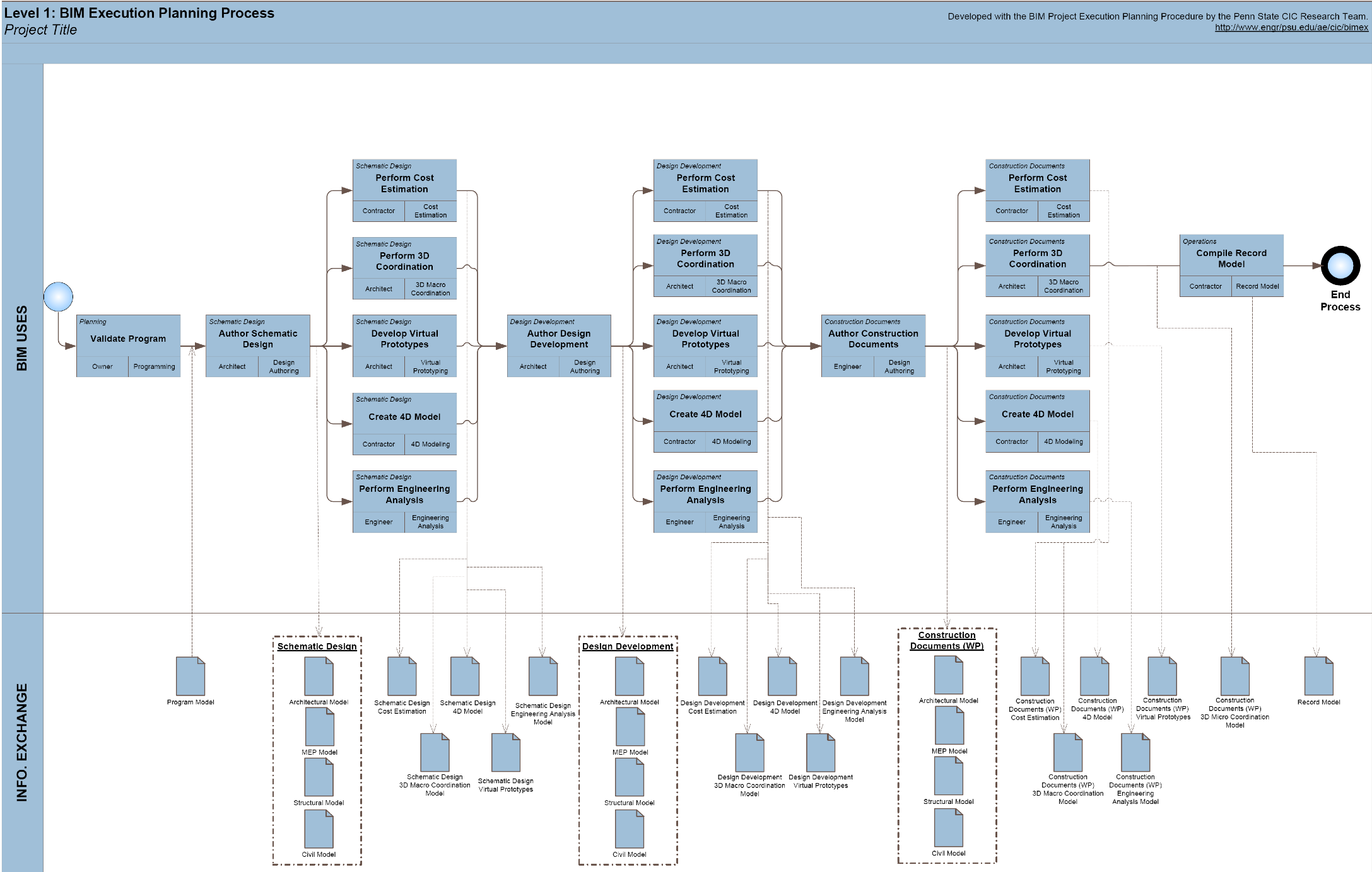
Appendix D Process Map Templates BIM Project Execution Planning
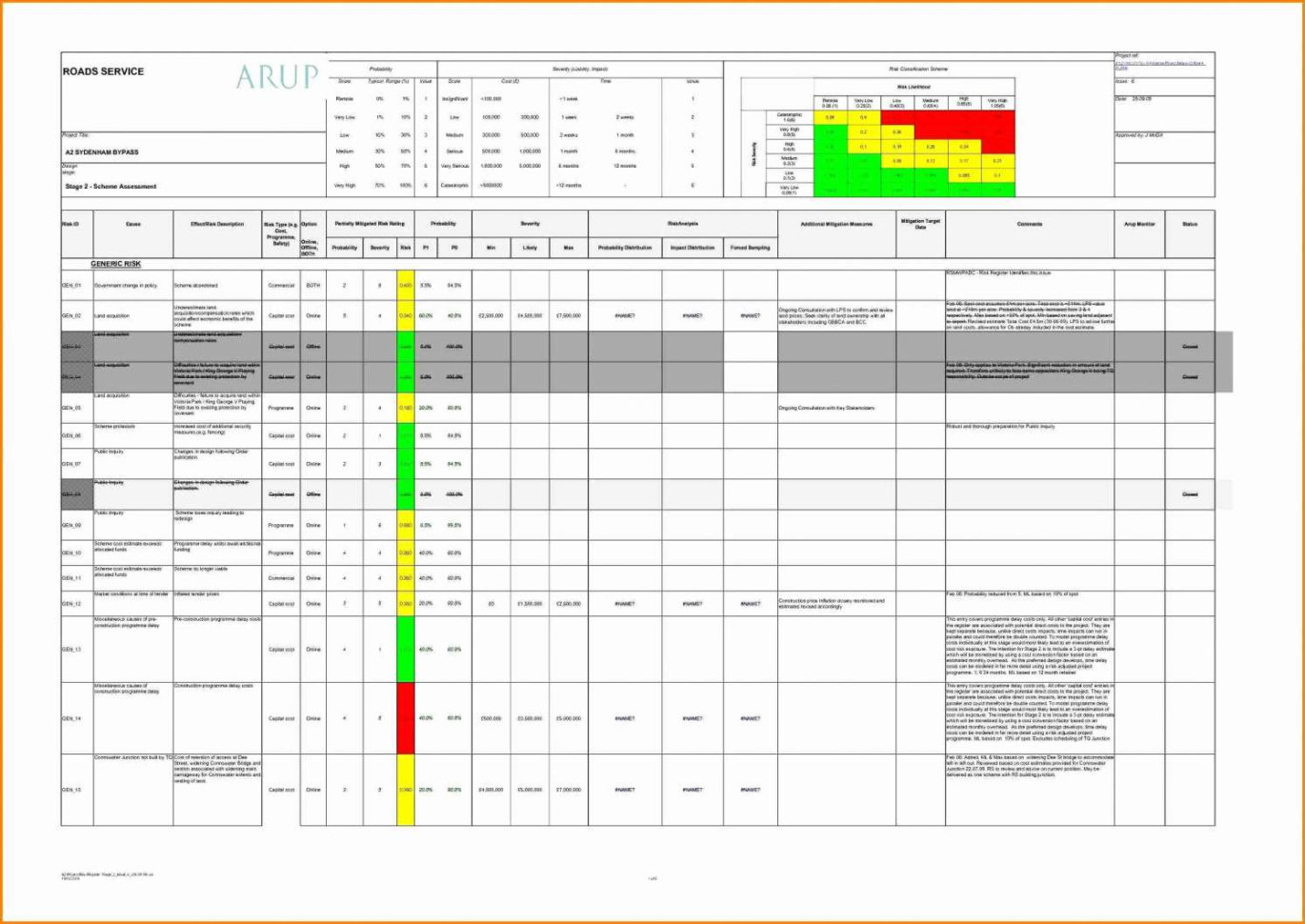
Project Resource Allocation Spreadsheet Template Regarding Excel
NITTF Produced Guides Templates
The U S Department of Homeland Security DHS or Department Insider Threat Program ITP was established as a DHS wide effort to manage insider threat matters The ITP detects prevents and mitigates threats posed to the Department by individuals who have or had authorized access to DHS facilities information equipment networks or systems
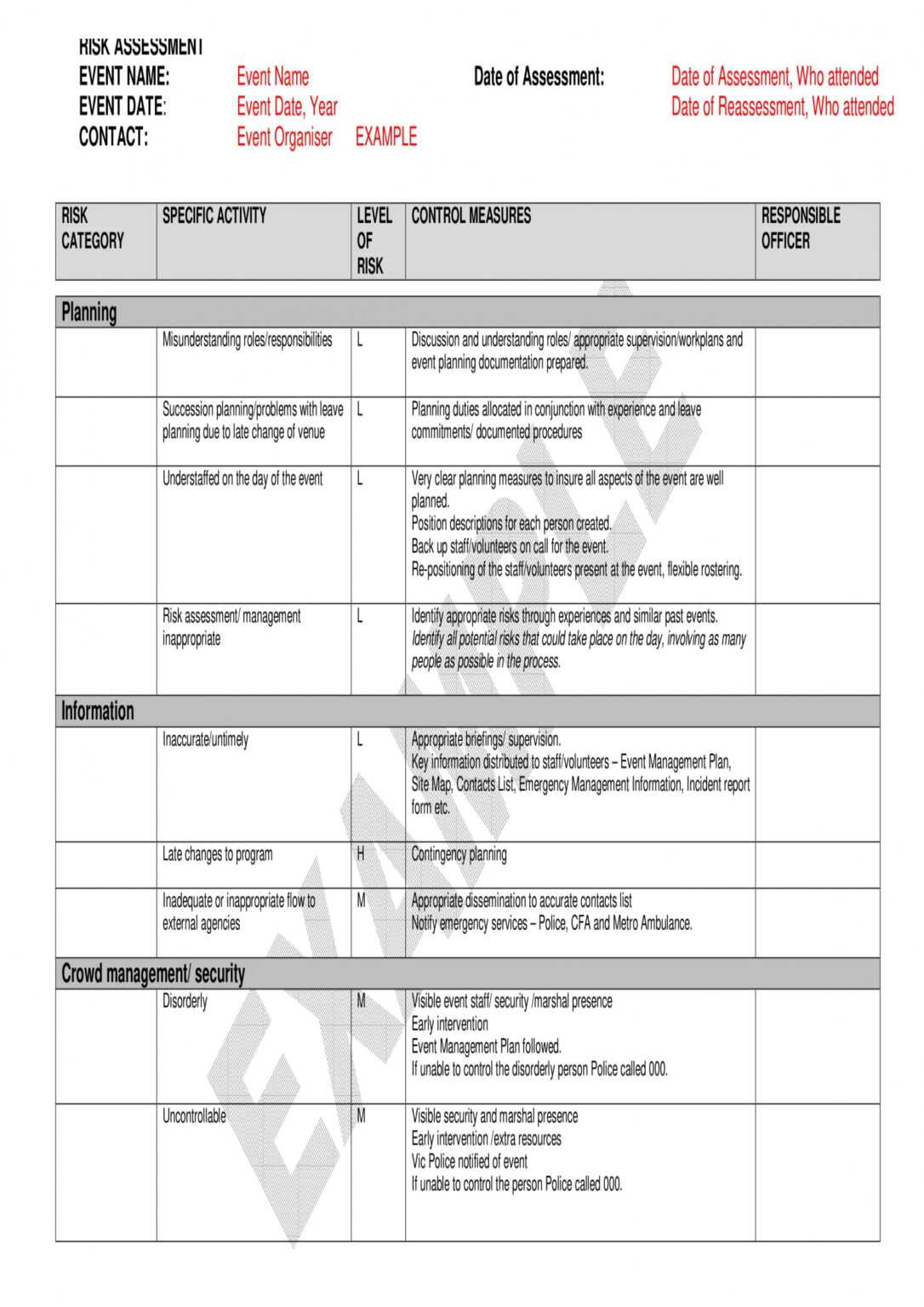
Free 4 Restaurant Risk Assessment Forms In Pdf Doc In Threat
The Insider Threat video uses security and behavior experts to discuss how insider threats manifest in a variety of ways including terrorism workplace violence and breaches of cybersecurity Understanding how to recognize and respond to these various types of insider threats whether non violent or violent increases an organization s
1. Insider Threat Program — Pre-Planning. In this phase, your organization will plan out the scope of the project, and identify internal assets and stakeholders. For SMBs, it's usually best to limit the scope, and execute a pilot insider threat program based around your organization's most pressing risks.
Span Class Result Type
Transportation Security Administration Insider Threat Roadmap 22 III 3 Mature the capability of the Transportation Systems Sector to mitigate threats by Fostering an agile insider threat posture and
![]()
2017 Insider Threat Guide
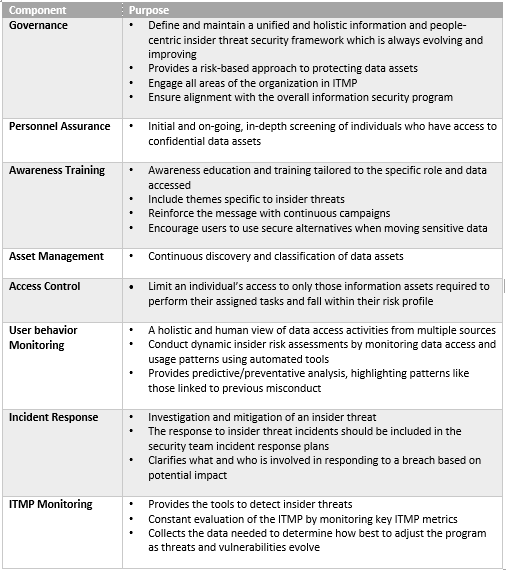
Building An Insider Threat Management Program Divurgent
Eninsider Threat Plan Template
The Insider Threat video uses security and behavior experts to discuss how insider threats manifest in a variety of ways including terrorism workplace violence and breaches of cybersecurity Understanding how to recognize and respond to these various types of insider threats whether non violent or violent increases an organization s
An insider threat is a security risk that originates from within the targeted organization It typically involves a current or former employee or business associate who has access to sensitive information or privileged accounts within the network of an organization and who misuses the access

How ENinsider Created An Expert Directory In WordPress

Cyber Incident Response Plan Template 100 Free InfoSec Careers Network

IT Project Communication Plan Template Google Docs Word Template

Security Risk Assessment Template In 2020 Mission Statement Template

How ENinsider Created An Expert Directory In WordPress