Eninsider Threat Policy Template - The program detects risks to classified information from insiders and addresses the risk of violence or other degradation by an insider afecting government or contractor resources including personnel facilities information equipment networks or systems II Scope and applicability Name of Organization is subject to insider threats and
The Intelligence Community Equal Employment Opportunity and Diversity EEOD Office is responsible for the overall management of the ODNI EEO and Diversity Program and provides IC wide oversight and guidance in developing implementing and measuring progress in EEO diversity and inclusion
Eninsider Threat Policy Template

Eninsider Threat Policy Template
eLearning: Insider Threat Awareness Course INT101.16. eLearning: Developing a Multidisciplinary Insider Threat Capability INT201.16. eLearning: Insider Threat Mitigation Responses INT210.16. eLearning: Preserving Investigative and Operational Viability in Insider Threat INT220.16. eLearning: Insider Threat Records Checks INT230.16.
Policy templates Insider risk management templates are pre defined policy conditions that define the types of risk indicators and risk scoring model used by the policy Each policy must have a template assigned in the policy creation wizard before the policy is created Insider risk management supports up to twenty policies for each policy
NITTF Produced Guides Templates
Assistant Director America s critical infrastructure assets systems and networks regardless of size or function are susceptible to disruption or harm by an insider or someone with institutional knowledge and current or prior authorized

Threat Assessment Template Free HQ Printable Documents
The insider threat mission is a dynamic effort requiring constant evaluation fresh perspectives and updated approaches
Policy Template Clinical Policy Monofilament Testing

Insider Threat Report SC Report Template Tenable
Span Class Result Type
Insider Threat Program Implementation A guide for developing and implementing an effective insider threat program for cleared defense contractors This PDF document provides an overview of the insider threat program requirements best practices and resources from the Florida Industrial Security Working Group

Investigation Policy Template Construction Documents And Templates
The Insider Threat video uses security and behavior experts to discuss how insider threats manifest in a variety of ways including terrorism workplace violence and breaches of cybersecurity Understanding how to recognize and respond to these various types of insider threats whether non violent or violent increases an organization s
Insider threats can include fraud, theft of intellectual property (IP) or trade secrets, unauthorized trading, espionage and IT infrastructure sabotage. 56%. 56% of respondents view data leakage/data loss prevention as a high priority for their organizations over the next 12 months. 56%. 56% of respondents view employees as the second most ...
Insider Threat Toolkit DCSA CDSE
Policy The U M Insider Threat Program ITP implements a process to deter detect prevent and mitigate or resolve behaviors and activities of trusted insiders that may present a witting or unwitting threat to Federally designated Sensitive Information information systems research environments and affected persons at U M

Fillable Online Policy Template FINAL Fax Email Print PdfFiller
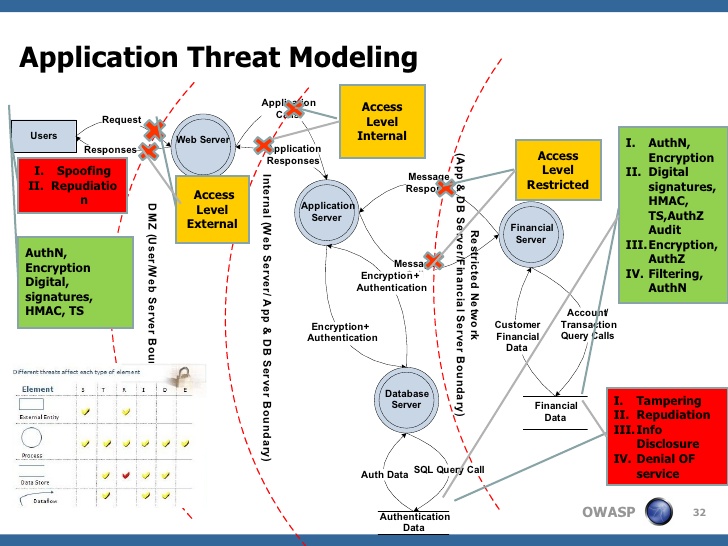
Threat Assessment Template Template Business
Eninsider Threat Policy Template
The Insider Threat video uses security and behavior experts to discuss how insider threats manifest in a variety of ways including terrorism workplace violence and breaches of cybersecurity Understanding how to recognize and respond to these various types of insider threats whether non violent or violent increases an organization s
The Intelligence Community Equal Employment Opportunity and Diversity EEOD Office is responsible for the overall management of the ODNI EEO and Diversity Program and provides IC wide oversight and guidance in developing implementing and measuring progress in EEO diversity and inclusion

Free Information Security Policy Template Uk Printable Templates
Physical Security Threat Assessment Template For Your Needs

Bomb Threat Checklist Fill And Sign Printable Template Online Gambaran
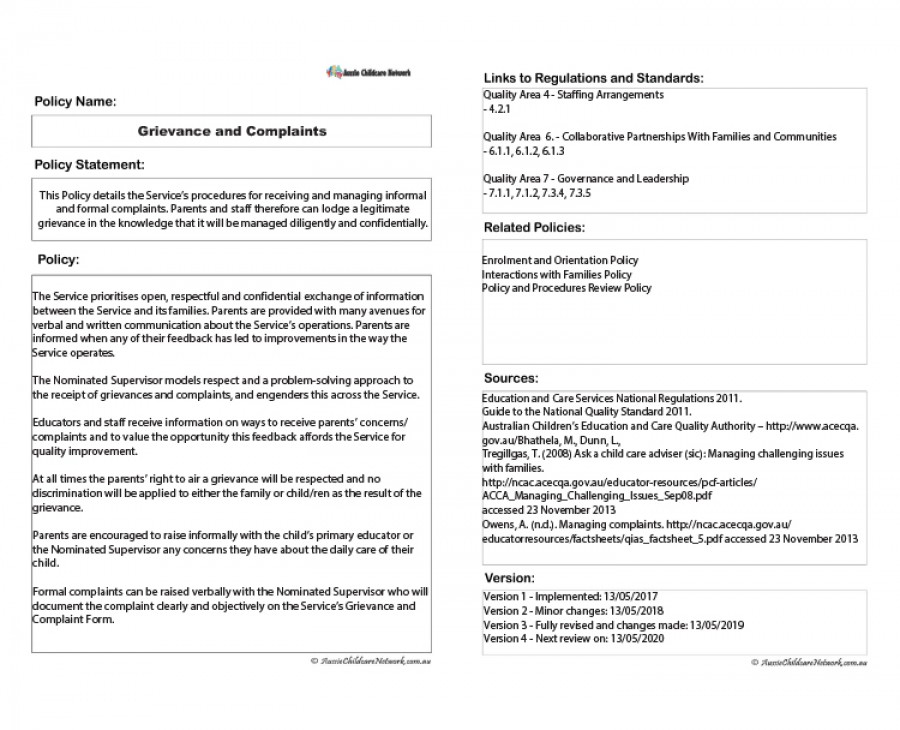
Policy Template Aussie Childcare Network
Medical Threat Assessment Templates At Regarding Threat Assessment