Eninsider Threat Program Template - ELearning Insider Threat Awareness Course INT101 16 eLearning Developing a Multidisciplinary Insider Threat Capability INT201 16 eLearning Insider Threat Mitigation Responses INT210 16 eLearning Preserving Investigative and Operational Viability in Insider Threat INT220 16 eLearning Insider Threat Records Checks INT230 16
Insider Threat In response to the Washington Navy Yard Shooting on September 16 2013 NISPOM Conforming Change 2 and Industrial Security Letter ISL 2016 02 effective May 18 2016 was released establishing requirements for industry s insider threat programs In December 2016 DCSA began verifying that insider threat program minimum
Eninsider Threat Program Template
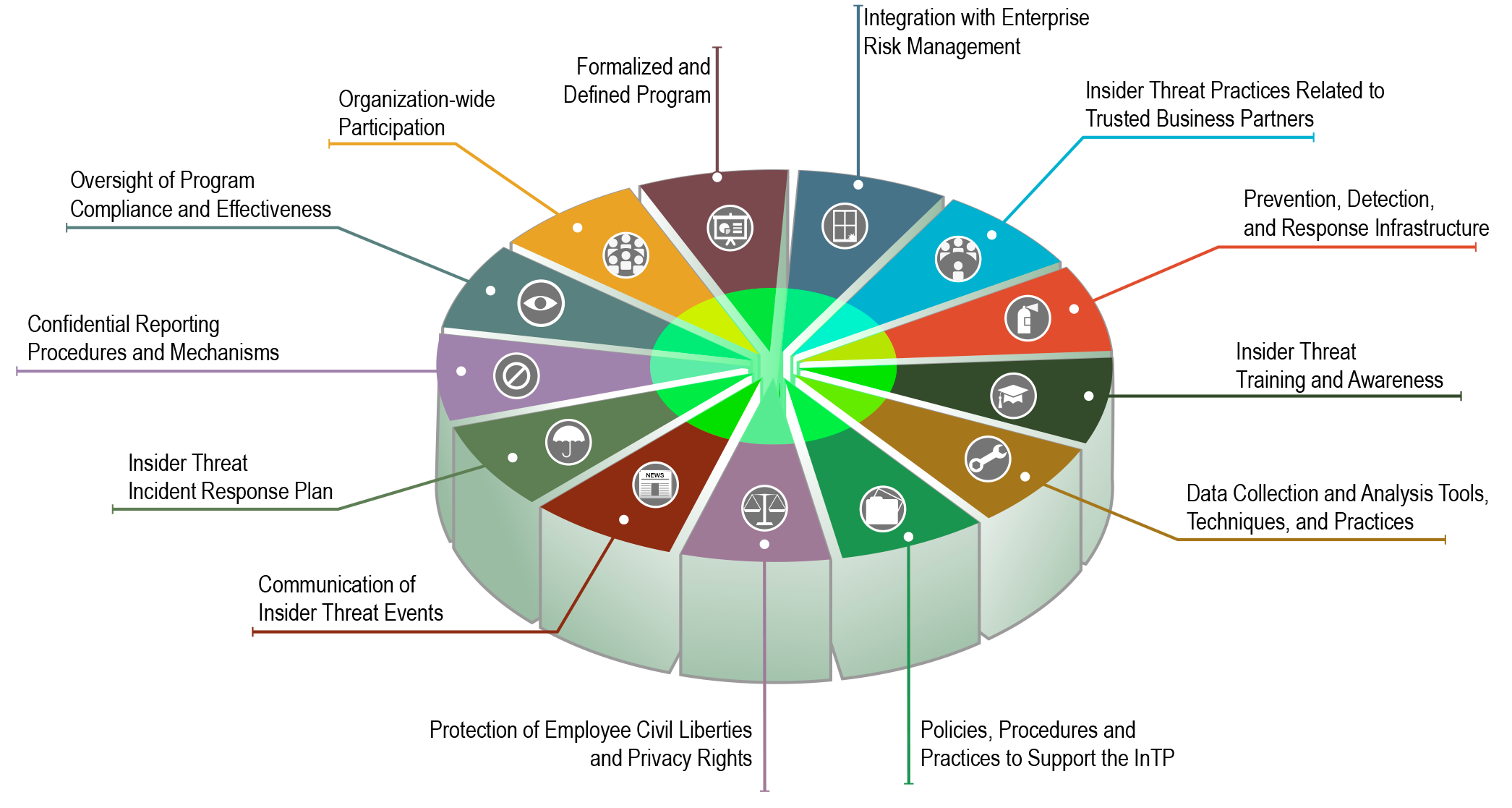
Eninsider Threat Program Template
The Intelligence Community Equal Employment Opportunity and Diversity (EEOD) Office is responsible for the overall management of the ODNI EEO and Diversity Program, and provides IC-wide oversight and guidance in developing, implementing, and measuring progress in EEO, diversity, and inclusion.
Insider Threat 101 Fact Sheet Physical Security Insider Threat Mitigation This fact sheet provides organizations a fundamental overview of insider threats and the key components to building an Insider Threat Mitigation Program
Insider Threat Defense Counterintelligence And Security Agency
Establishing a Foundation and Building an Insider Threat Program Establishing a brand new process function or program can be daunting Some of the challenges include determining where to start researching whether it has been done successfully in the past and if it has discovering the best practices and frameworks that can be used as a
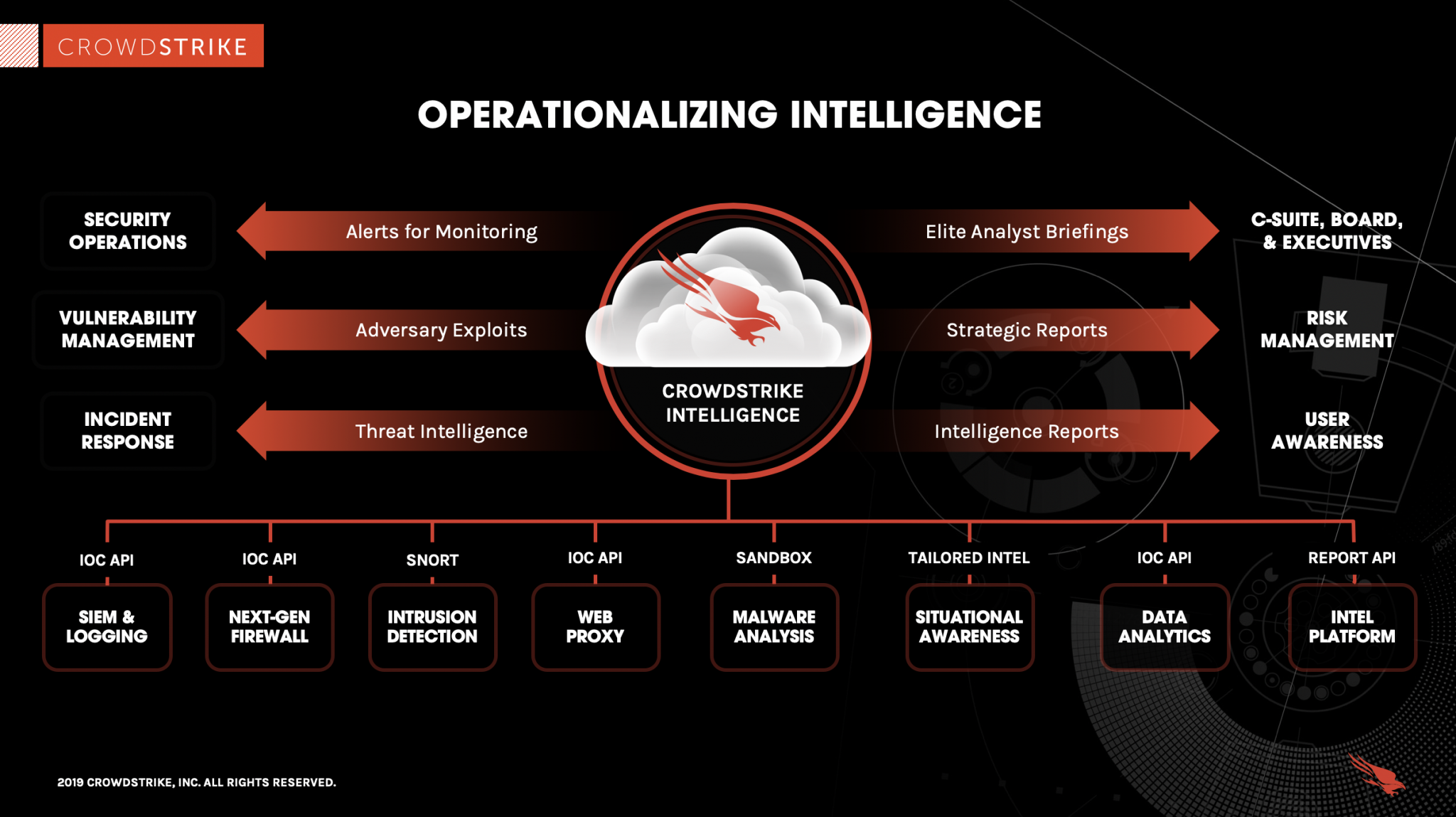
What Is Cyber Threat Intelligence Beginner s Guide
1 Insider Threat Program Pre Planning In this phase your organization will plan out the scope of the project and identify internal assets and stakeholders For SMBs it s usually best to limit the scope and execute a pilot insider threat program based around your organization s most pressing risks

Insider Threat Report SC Report Template Tenable

Why Is The Success Of The Insider Threat Program AlejandrogroAvery
Insider Threat Toolkit DCSA CDSE
Insider Threat Program Implementation A guide for developing and implementing an effective insider threat program for cleared defense contractors This PDF document provides an overview of the insider threat program requirements best practices and resources from the Florida Industrial Security Working Group

Army Solution Breaks New Ground In Cybersecurity Article The United
Assistant Director America s critical infrastructure assets systems and networks regardless of size or function are susceptible to disruption or harm by an insider or someone with institutional knowledge and current or prior authorized
CISA created the IRMPE tool in collaboration with Carnegie Mellon University's Software Engineering Institute to help stakeholders gauge their readiness for a potential insider threat incident. The tool pulls from insider threat planning and preparedness resources to allow users to evaluate the maturity of their insider threat program in one ...
NITTF Produced Guides Templates
INTRODUCTION This job aid gives Department of Defense DOD staf and contractors an overview of the insider threat program requirements for Industry as outlined in the National Industrial Security Program Operating Manual NISPOM that became efective as a federal rule in accordance with 32 Code of Federal Regulations Part 117 also known as

Threat Assessment Template Template Business

Guide To Insider Threats SoftActivity
Eninsider Threat Program Template
Assistant Director America s critical infrastructure assets systems and networks regardless of size or function are susceptible to disruption or harm by an insider or someone with institutional knowledge and current or prior authorized
Insider Threat In response to the Washington Navy Yard Shooting on September 16 2013 NISPOM Conforming Change 2 and Industrial Security Letter ISL 2016 02 effective May 18 2016 was released establishing requirements for industry s insider threat programs In December 2016 DCSA began verifying that insider threat program minimum
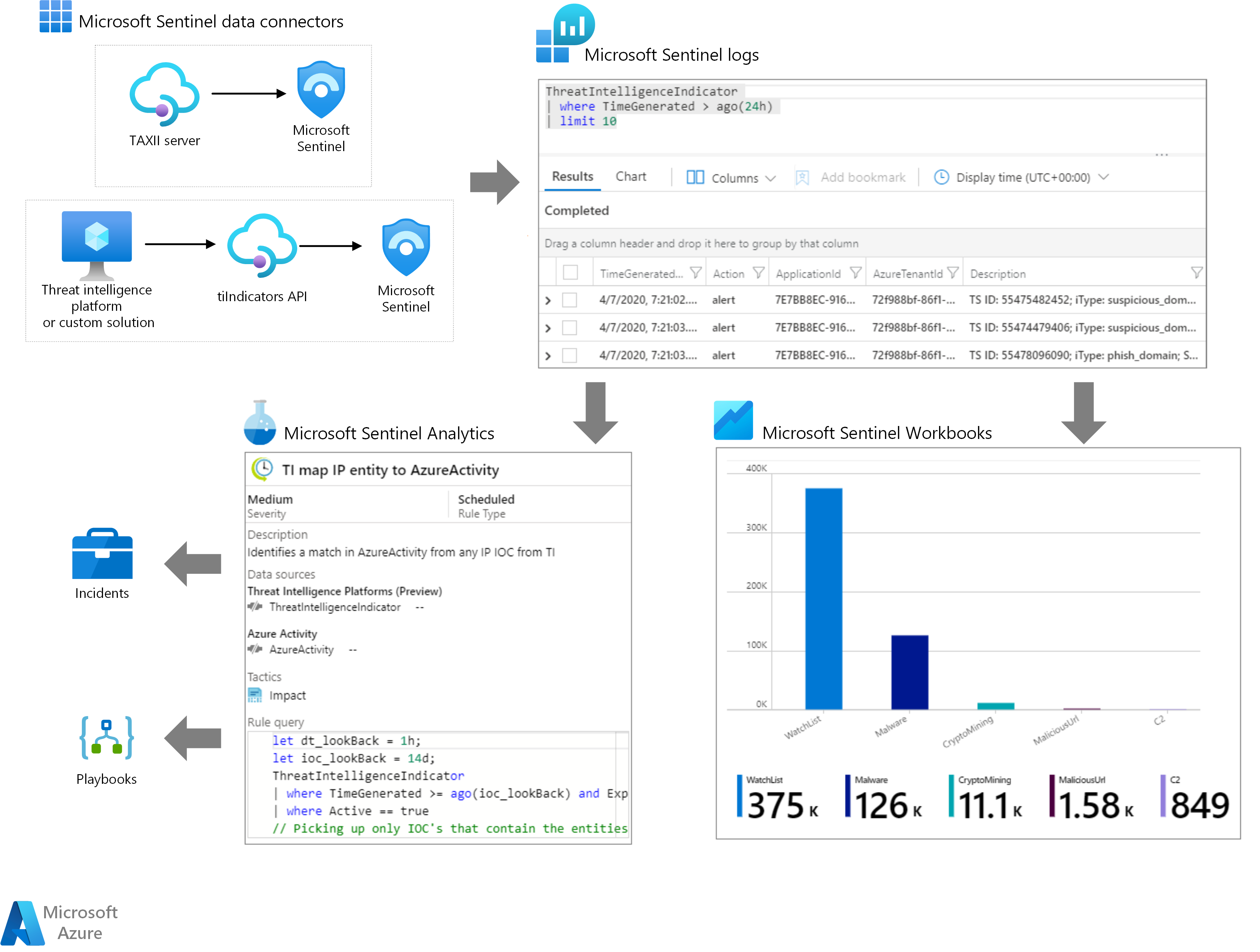
Cyber Threat Intelligence In Microsoft Sentinel Azure Example

Threat Vulnerability Dashboard Information Security Risk Management

Maturing A Threat Intelligence Program SC Media UK

How ENinsider Created An Expert Directory In WordPress

Threat Handwriting Image