Enleast Privilege Policy Template - In this article The information security principle of least privilege asserts that users and applications should be granted access only to the data and operations they require to perform their jobs
We recommend using policies that grant least privilege or granting only the permissions required to perform a task The most secure way to grant least privilege is to write a customer managed policy with only the permissions needed by your team You must create a process to allow your team to request more permissions when necessary It takes time and expertise to
Enleast Privilege Policy Template

Enleast Privilege Policy Template
The principle of least privilege is a minimum access policy that centrally manages and secures privileged credentials, and only allows users access to the least amount of required privileges. It also needs to have flexible controls that can balance compliance requirements with cybersecurity, operational functions, and the end-user experience.
If you re not familiar with creating policies you can follow the full instructions in the IAM documentation Figure 1 Use the visual editor to create a policy Begin by choosing the first service S3 to grant access to as shown in Figure 2 You can only choose one service at a time so you ll need to add DynamoDB after
Getting Started With Managed Policies AWS Identity And Access Management
Privileged access is typically granted to system administrators network administrators or other such employees whose job duties require access to sensitive data residing on a system or network This data can be paper or electronic data For the purposes of this policy application and other developers are also considered privileged

Fillable Online Policy Template FINAL Fax Email Print PdfFiller
The principle of least privilege POLP requires giving each user service and application only the permissions needed to perform their work and no more It is one of the most important concepts in network and system security No matter how technically skilled or trustworthy a user is they should have access to only the network resources they

Free Acceptable Use Policy Template
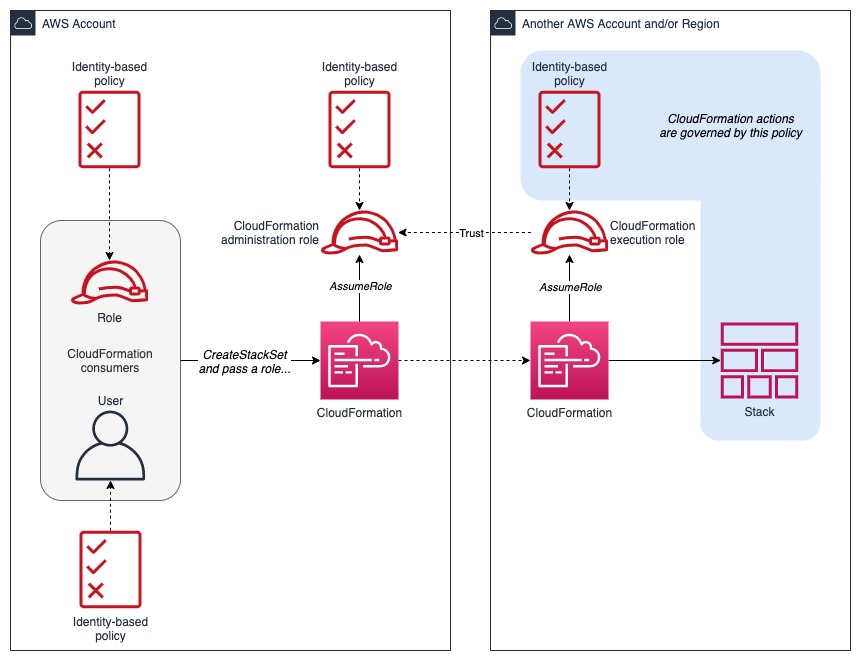
How To Implement The Principle Of Least Privilege With CloudFormation
Increase Application Security With The Principle Of Least Privilege
The Principle of Least Privilege PoLP is a foundational security principle that ensures users receive only the access needed to fulfill their roles By following PoLP organizations limit access to essential data resources and applications granting users merely the minimum permissions required for their tasks and bolstering overall system
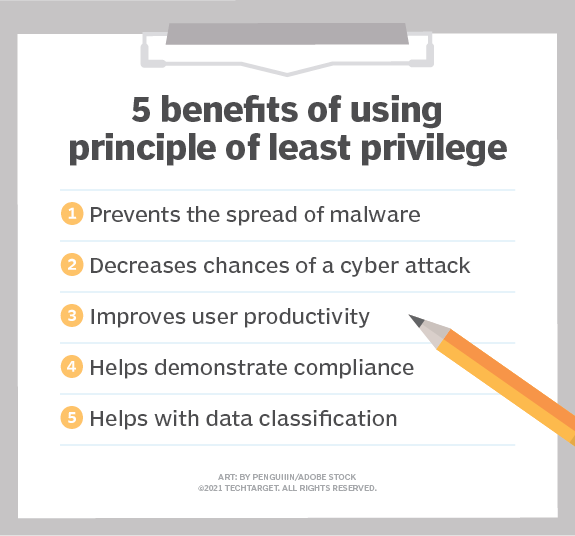
What Is The Principle Of Least Privilege Definition From TechTarget
Developing least privilege IAM roles As you develop a Lambda function you expand the scope of this policy to enable access to other resources For example for a function that processes objects put into an S3 bucket it requires read access to objects stored in that bucket Do not grant the function broader permissions to write or delete data
cisecurity.orgms-isac/ NIST Function: Protect Page 4 NIST FUNCTION: Protect Protect: Identity Management and Access Control (PR.AC) PR.AC-1 Identities and credentials are issued, managed, verified, revoked, and audited for
Principle Of Least Privilege Definition Methods Examples
The principle of least privilege or least privilege access is a cyber security best practice that requires limiting users to the privileges necessary to perform a specific task It is the basis of the zero trust model however zero trust model is much more comprehensive Security professionals usually regard this principle as concerning

Insurance Policy Templates 12 Printable Word Excel Formats

Complaints Policy Template Free PRINTABLE TEMPLATES
Enleast Privilege Policy Template
Developing least privilege IAM roles As you develop a Lambda function you expand the scope of this policy to enable access to other resources For example for a function that processes objects put into an S3 bucket it requires read access to objects stored in that bucket Do not grant the function broader permissions to write or delete data
We recommend using policies that grant least privilege or granting only the permissions required to perform a task The most secure way to grant least privilege is to write a customer managed policy with only the permissions needed by your team You must create a process to allow your team to request more permissions when necessary It takes time and expertise to
Acceptable Use Policy Template TermsFeed
Policy Template Aussie Childcare Network

Whistleblower Policy Template Banking And Fintech Policies Templates

Security Policy Template Free Database

Redundancy Policy Template Modern HR UK