Ensystem Hardening Policy Template - Some of the general steps included in the Server Hardening Procedure are 2 1 Installing the operating system from an IS approved source 2 2 Applying vendor supplied patches 2 3 Removing unnecessary software system services and drivers 2 4 Setting security parameters file protections and enabling audit logging
Operating system hardening methods include Applying the latest updates released from the operating system developer i e Microsoft Apple Enabling built in security features such as Microsoft Defender or using 3rd party EPP EDR software Deleting unneeded drivers and updating the ones that are used
Ensystem Hardening Policy Template

Ensystem Hardening Policy Template
Operating system hardening Operating system selection. When selecting operating systems, it is important that an organisation preferences vendors that have demonstrated a commitment to secure-by-design and secure-by-default principles, use of memory-safe programming languages where possible (such as C#, Go, Java, Ruby, Rust and Swift), secure programming practices, and maintaining the security ...
Infrastructure Hardening Policy Page 2 of 8 Document Control Document Storage Document Title Hardening Policy Document Location C Ruskwig docs iso 27002 Infrastructure Hardening Policy RW doc Version History Version No Version
System Hardening Guidelines Critical Best Practices
One that cover patching and AV etc Okay it might be difficult to find a generic baseline because it usually comes down to each organization as every organizations do things in their own way and have different requirements needs For the antivirus maybe the antivirus software provider might have some baseline but here as well every
Window Server 2003 Hardening Guidelines Minimum Security Standards
A collection of awesome security hardening guides tools and other resources GitHub decalage2 awesome security hardening A collection of awesome security hardening guides tools and other resources

What Is System Hardening Intel

Muster Plam Hardening 35 Farben Isoplam Stempelbeton
Span Class Result Type
The hardening checklists are based on the comprehensive checklists produced by the Center for Internet Security CIS when possible The Information Security Office has distilled the CIS lists down to the most critical steps for your systems with a particular focus on configuration issues that are unique to the computing environment at The University of Texas at Austin

Server Hardening Policy Examples And Tips
Hardening A System or Device Why Is It Important If two things are to be gained from this document it s that to secure and have a trustworthy device it must be hardened
System hardening is the process of securing a server or computer system by minimizing its attack surface, or surface of vulnerability, and potential attack vectors. It's a form of cyberattack protection that involves closing system loopholes that cyberattackers frequently use to exploit the system and gain access to users' sensitive data.
Guidelines For System Hardening Cyber Gov Au
CIS Hardening and Configuration Security Guide The Center for Internet Security CIS published an updated version for the CIS Controls CIS Controls v8 The CIS Controls are a set of gold standard guidelines for organizations facing data security issues These controls were developed to simplify and help IT ops and security teams to remain

System Hardening Recommendations FINAL
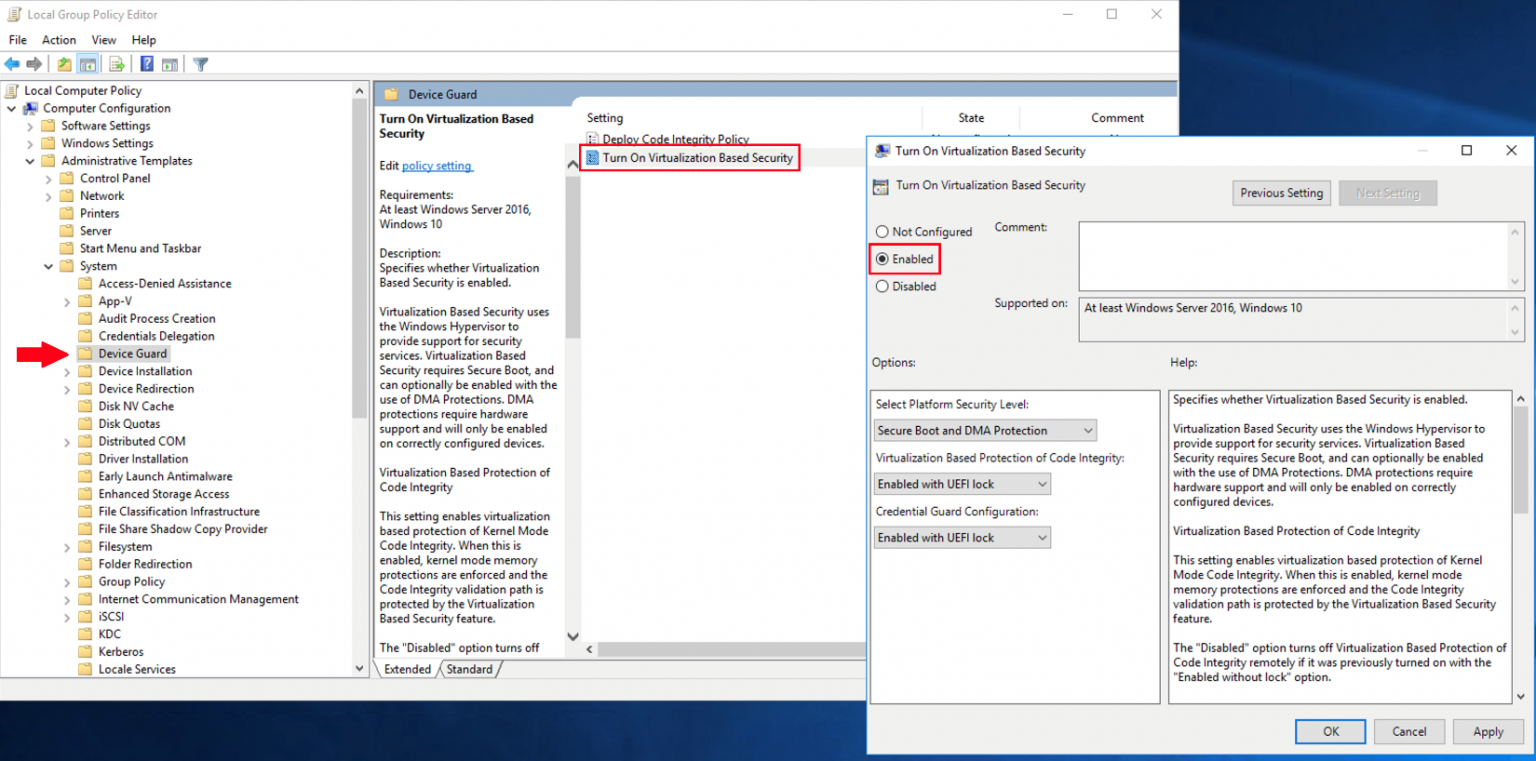
Hardening Your Windows Server In 2020 Network Wrangler Tech Blog
Ensystem Hardening Policy Template
Hardening A System or Device Why Is It Important If two things are to be gained from this document it s that to secure and have a trustworthy device it must be hardened
Operating system hardening methods include Applying the latest updates released from the operating system developer i e Microsoft Apple Enabling built in security features such as Microsoft Defender or using 3rd party EPP EDR software Deleting unneeded drivers and updating the ones that are used
Windows Server Security Best Practices

ISMS Policy ISO 27001 Institute

System Hardening Standards How To Comply With PCI Requirement 2 2
What Is System Hardening Standards And Best Practices Chef
Intune ACSC Windows Hardening Guidelines FIPSAlgorithmPolicy ps1 At
