Ensystem Security Plan Template Nist 800 53 Rev 5 - The organization Develops a security plan for the information system that Is consistent with the organization s enterprise architecture Explicitly defines the authorization boundary for the system Describes the operational context of the information system in terms of missions and business processes Provides the security categorization of the information system including supporting
Abstract This publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets individuals other organizations and the Nation from a diverse set of threats and risks including hostile attacks human errors natural disasters structural failures
Ensystem Security Plan Template Nist 800 53 Rev 5
Ensystem Security Plan Template Nist 800 53 Rev 5
System security and privacy plans can also be used in the design and development of systems in support of life cycle-based security and privacy engineering processes. System security and privacy plans are living documents that are updated and adapted throughout the system development life cycle (e.g., during capability determination, analysis ...
Nist sp 800 53 rev 5 security and privacy controls for information systems and organizations i
SP 800 53 Rev 5 Security And Privacy Controls For Information CSRC
This publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and organizations within an effective risk management framework The assessment procedures executed at various phases of the system development life cycle are consistent with the security and privacy controls in NIST Special Publication 800 53
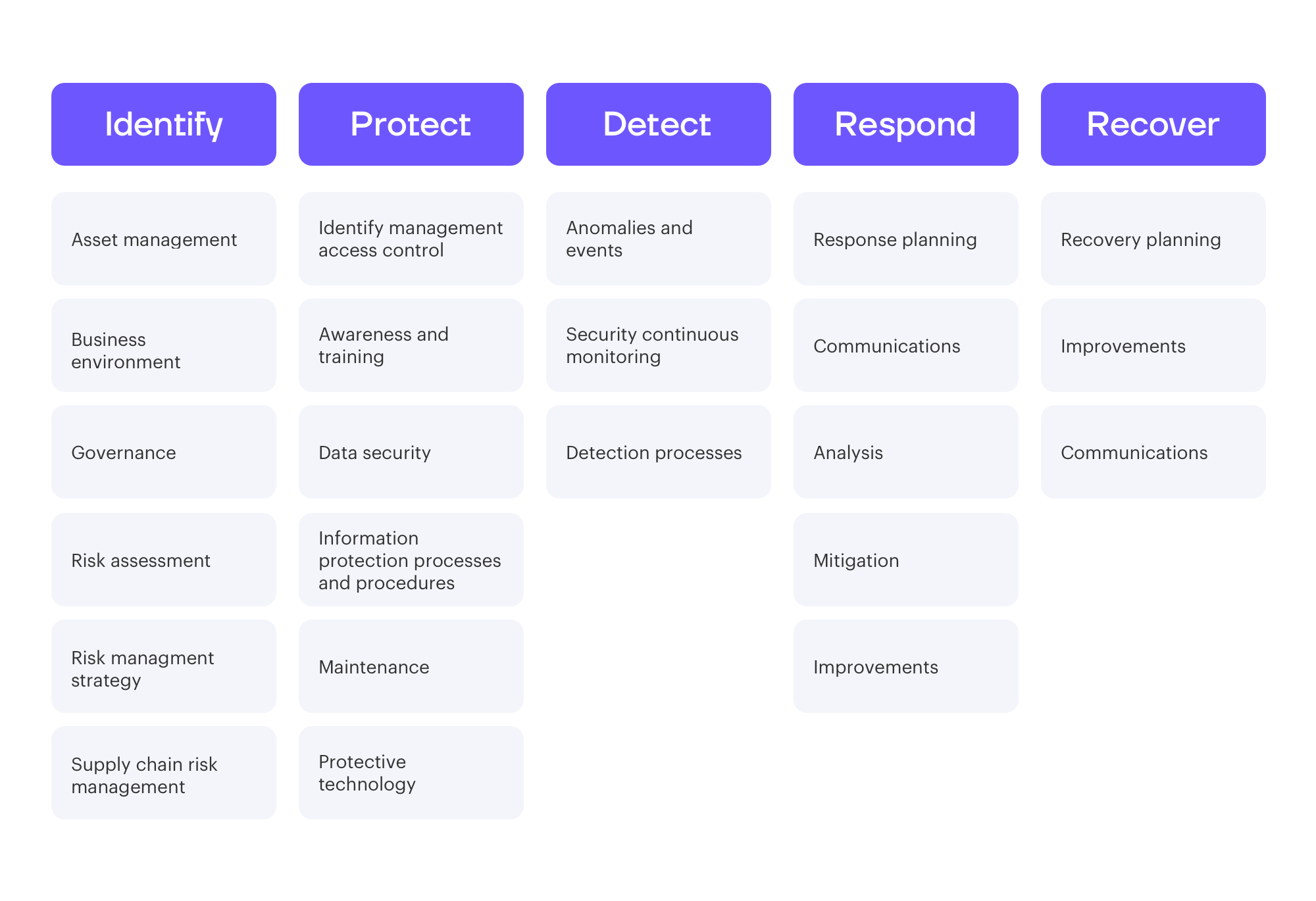
Nist 800 53 Rev 5 Controls Spreadsheet Inside Nist 800 53 Rev 3
The OSCAL system security plan SSP model represents a description of the control implementation of an information system The SSP model is part of the OSCAL implementation layer The OSCAL SSP model enables full modeling of highly granular SSP content including points of contact system characteristics and control satisfaction descriptions

Nist 800 53 Rev 4 Controls Spreadsheet 2 Qualads
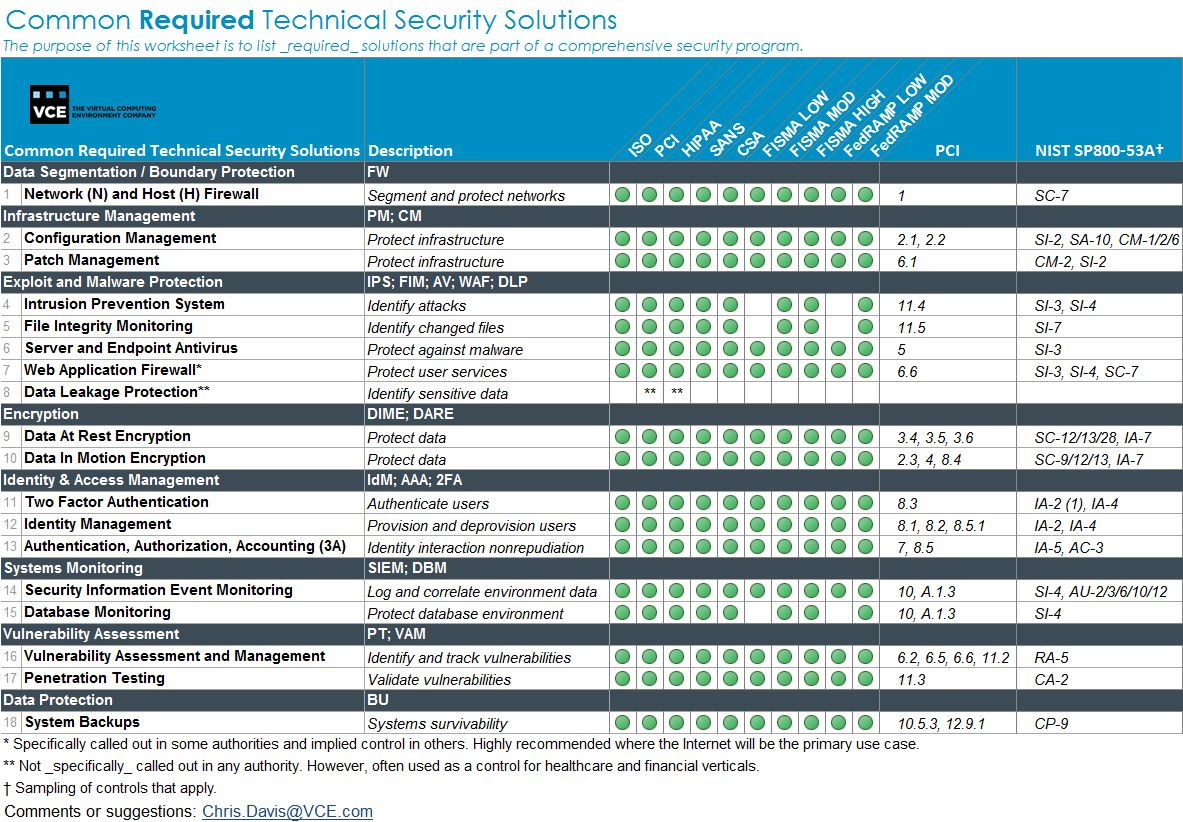
Nist Sp 800 53 Rev 4 Spreadsheet With Nist 800 53 Rev 4 Excel
PL 2 System Security Plan CSF Tools Identity Digital
The FedRAMP Program Management Office PMO updated the FedRAMP documentation and templates to reflect the changes in NIST SP 800 53 Rev 5 and developed guidance to assist Cloud Service Providers CSPs in transitioning to Rev 5 Please refer to the FAQ page for additional information d Rev 5 documents can be found on the Documents and

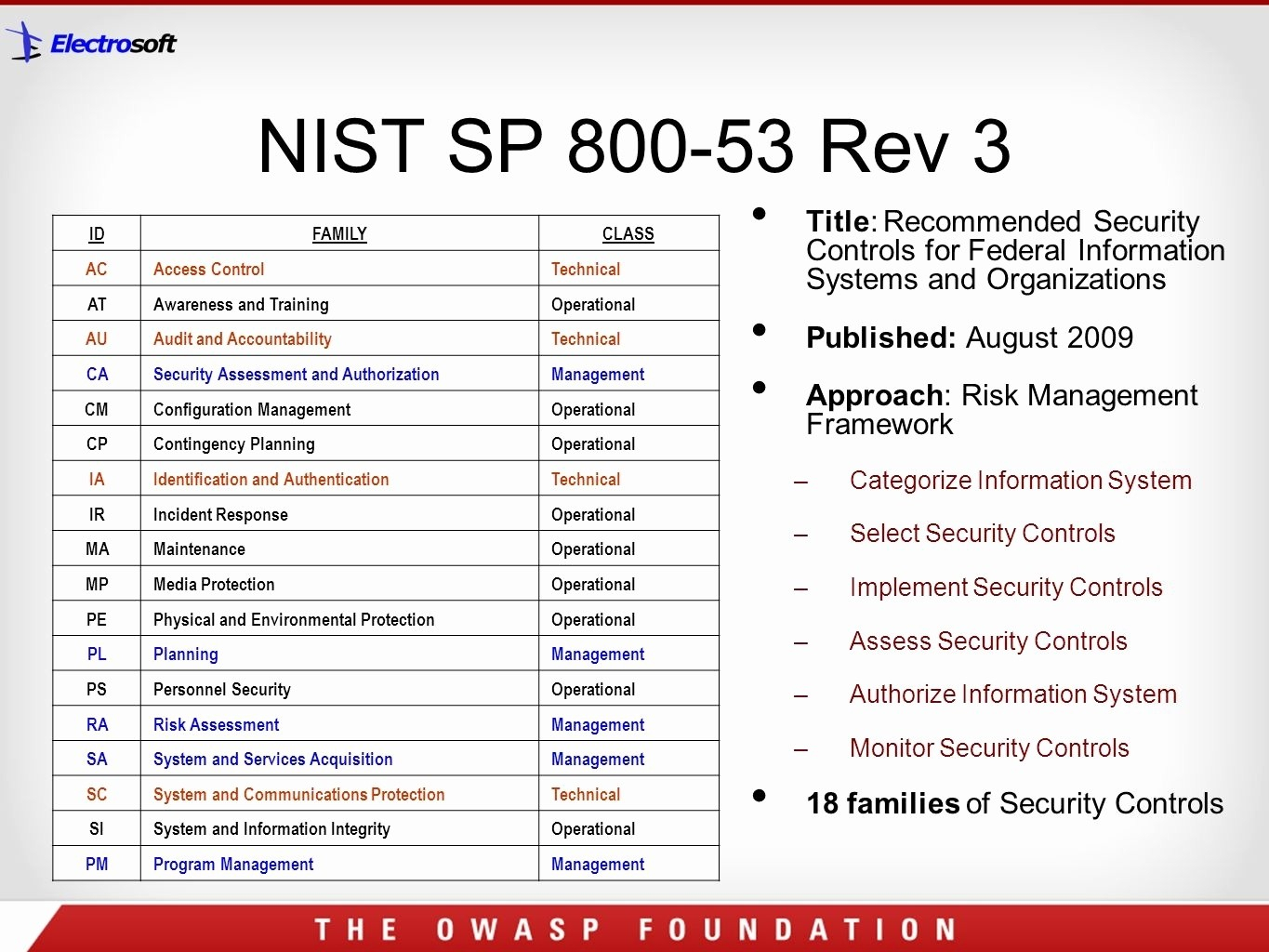
NIST 800 53 Framework
Guide for Developing Security Plans for Federal Information Systems Reports on Information Systems Technology The Information Technology Laboratory ITL at the National Institute of Standards and
Changing the access keys on a regular schedule is a security best practice. It shortens the period an access key is active and reduces the business impact if the keys are compromised. This rule requires an access key rotation value (Config Default: 90). The actual value should reflect your organization's policies.
PL 2 System Security And Privacy Plans CSF Tools
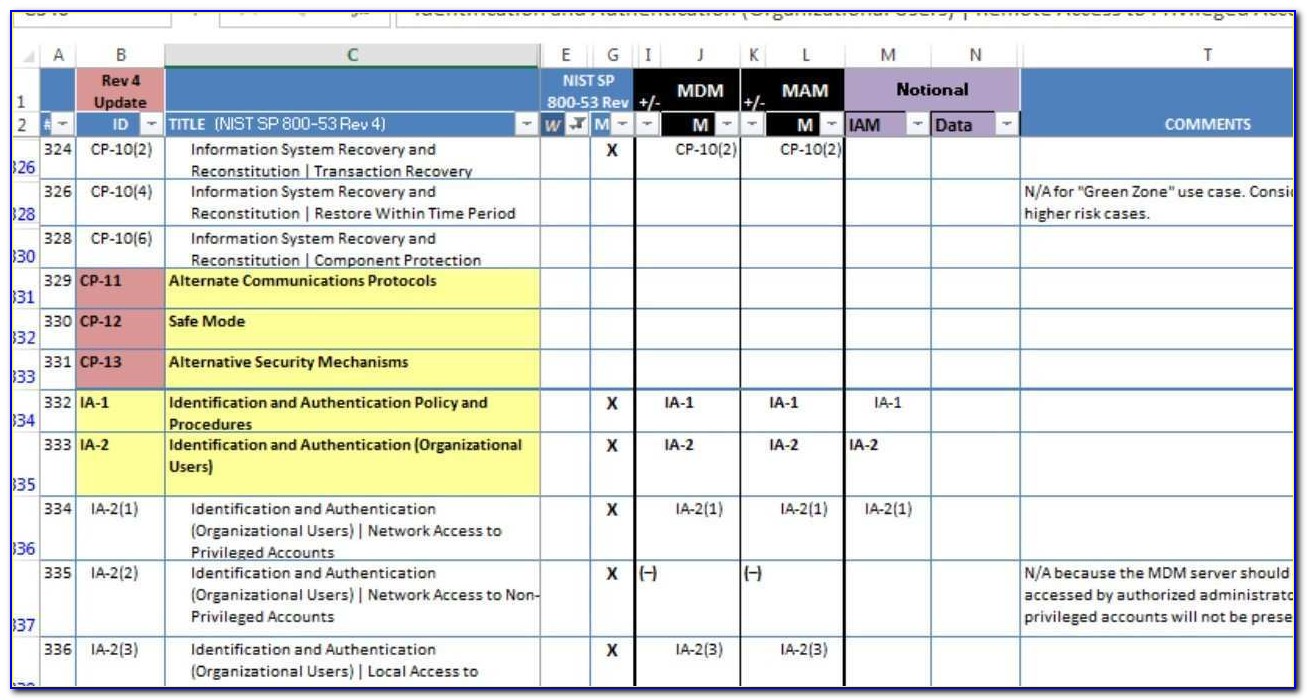
The control is assigned a class SP800 53 This serves as an indicator to a downstream processor of the control s origin with respect to the catalog or catalog type with implications for related expectations including expectations in detail regarding how the control and its contents may be structured The control ID is ac 1

NIST SP 800 53 Rev 5 Initial Public Draft Published Musings
Nist 800 Risk Assessment Template Example Cybersecurity Risk Porn Sex
Ensystem Security Plan Template Nist 800 53 Rev 5
Guide for Developing Security Plans for Federal Information Systems Reports on Information Systems Technology The Information Technology Laboratory ITL at the National Institute of Standards and
Abstract This publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets individuals other organizations and the Nation from a diverse set of threats and risks including hostile attacks human errors natural disasters structural failures
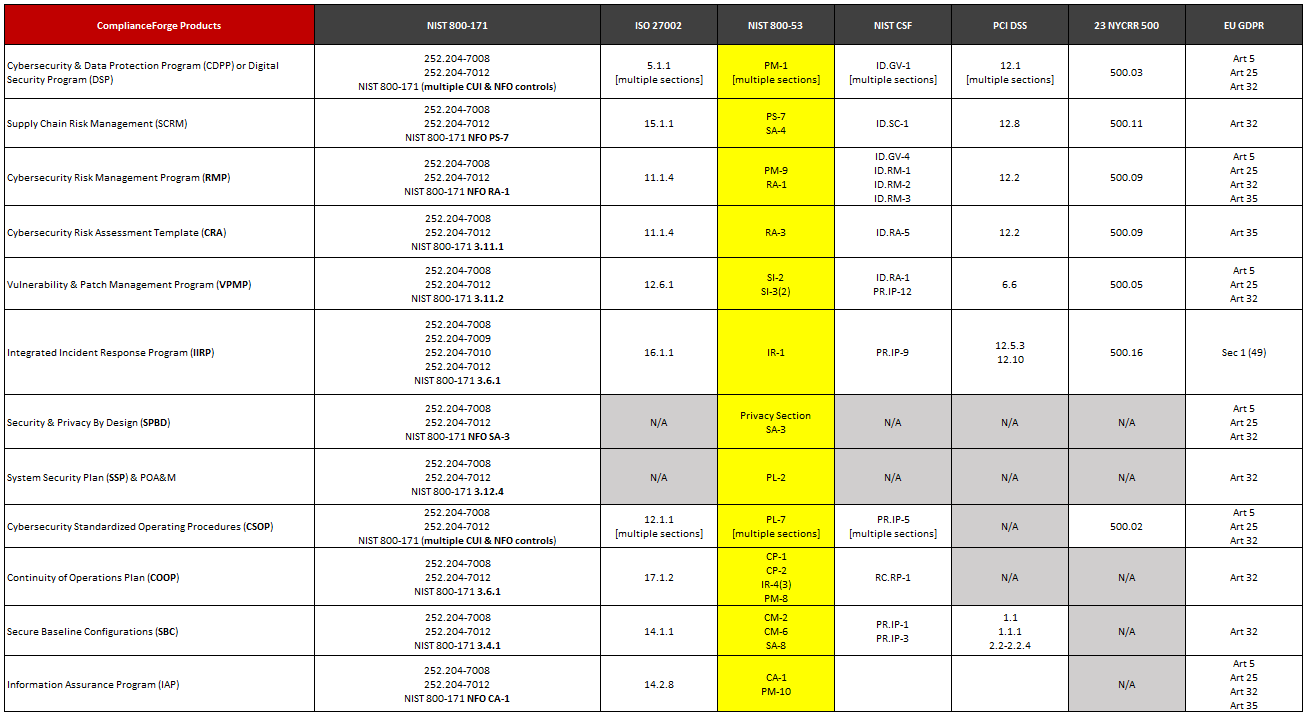
NIST SP 800 53 R5 Moderate Baseline Policies Standards Procedures
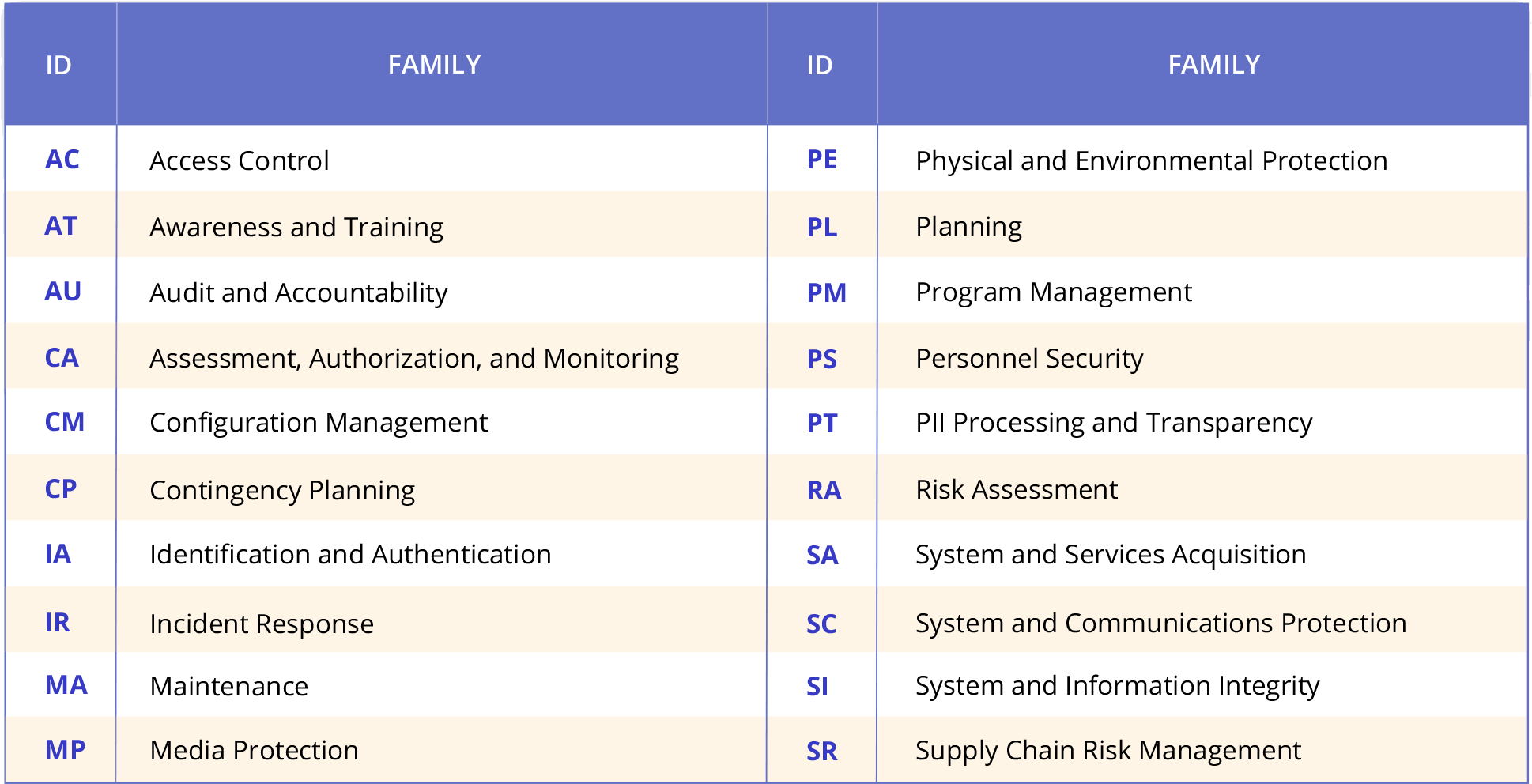
Ultimate Guide To NIST SP 800 53 Control Families And More
Nist 800 Risk Assessment Template Https Www Mitre Org Sites Default
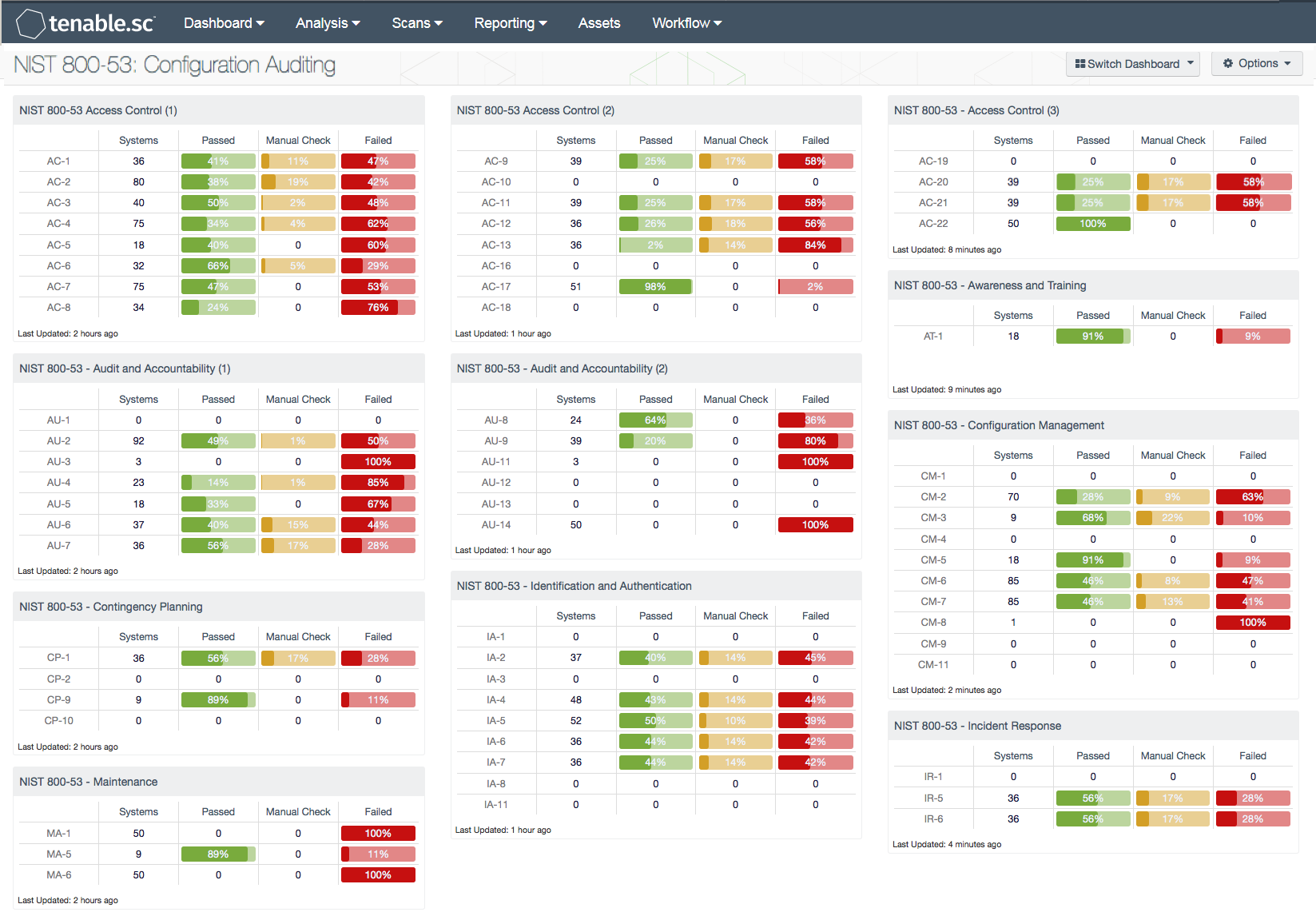
NIST 800 53 Configuration Auditing SC Dashboard Tenable
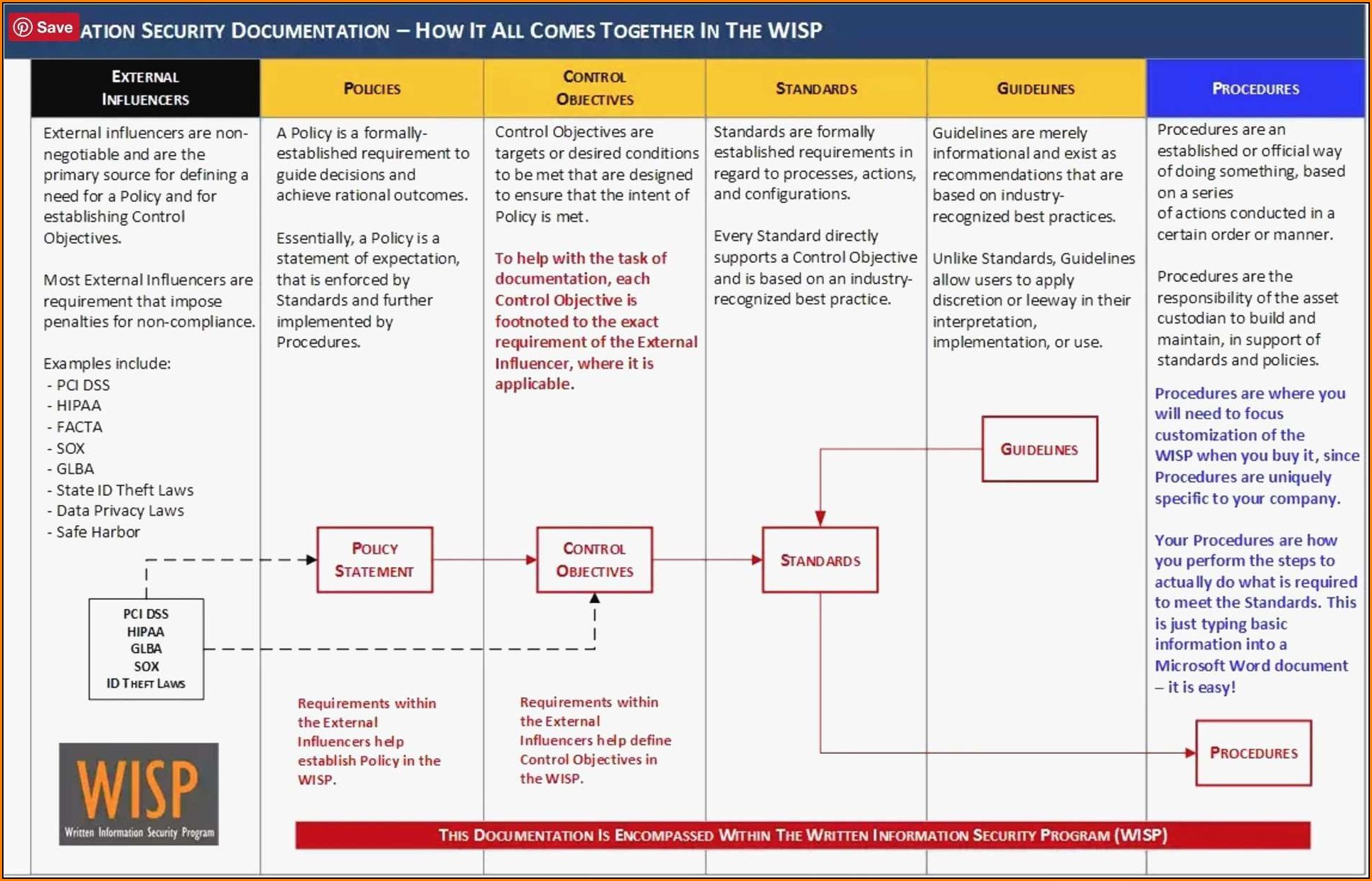
Security Incident Report Template Nist Template 1 Resume Examples