Enuser Access Review Policy Template - How to conduct a user access review Step 1 Define your access management policy At minimum a user access management policy should include the following An inventory of enterprise assets List
Conducted periodically e g monthly or quarterly or during role changes a User Access Review is an essential part of your cloud security toolkit helping you create an inventory of user accounts and their privileges and verify their appropriateness based on job roles Managers or system owners often participate in the review to confirm the
Enuser Access Review Policy Template
Enuser Access Review Policy Template
1. Define the scope of the user access review. Defining the scope of the user access review process is crucial, as it will help you conduct the audit in a more structured, timely, and efficient manner. It is a good idea to prioritize the accounts that have the highest risk profiles, as this will speed up the process and make it more efficient.
User access review process Now that you understand the benefits of user access reviews it s time to map out each step of the process 1 Inventory your tools and users To start inventory all current tools and technologies that you use Then list all users including internal and external users as well as users who have been terminated
The Essential User Access Review Template Checklist Download
A user access review can be swift effective and painless if you keep your access control policies up to date and implement globally and industry recognized security procedures We ve gathered six best practices for advancing your organization s user access reviews 1 Regularly update your access management policy
Access Control Policy Template Free
Now let s discuss the steps to automate the access review process Step 1 Open Zluri s main interface and go to the Access Certification module To create an access certification click on Create a New Certification Step 2 Now assign a suitable certification name and assign a responsive owner

Use The Graph API To Work With Azure AD Access Reviews Office 365 For
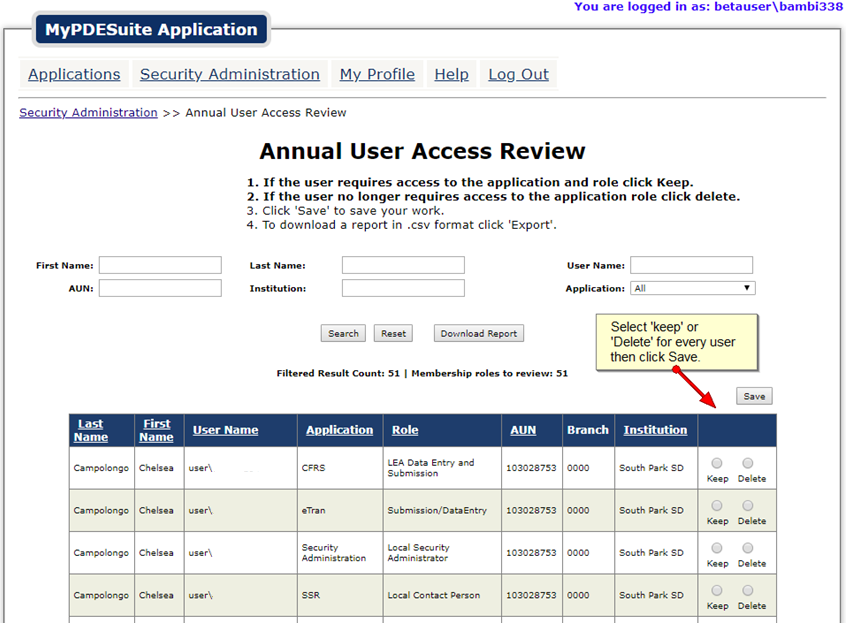
Annual User Access Review
Manage Best Practices To Conduct A User Access Review LinkedIn
User entitlement reviews ensure only authorized users have access to essential systems and data Uncover the steps of a user access review and helpful best practices Controlling and regularly reviewing which employees have access to which systems and data aren t just enterprise Enjoy this article as well as all of our content including E

Merchant Services Program Policy Template Banking And Fintech
1 Create and keep an access management policy up to date Any organization must have an access management policy and you must Create a list of data and resources you need to protect Create a list of all user roles levels and access types Identify controls tools and approaches for secure access
Step 3: Under the setup certification, choose how you want to review users' access: either by Application or Users. Note: if you select to review access by Application, add the application to audit users' access. Step 4: Then choose a primary reviewer and a fallback reviewer from the drop-down menu.
What Is A User Access Review Best Practices Checklist
The entitlement review definition is simple a review of user access permissions and other rights The goal of a user entitlement review is to ensure that each user in the IT environment has access to the data they need to do their job and nothing more the principle of least privilege A structured and regular entitlement review process
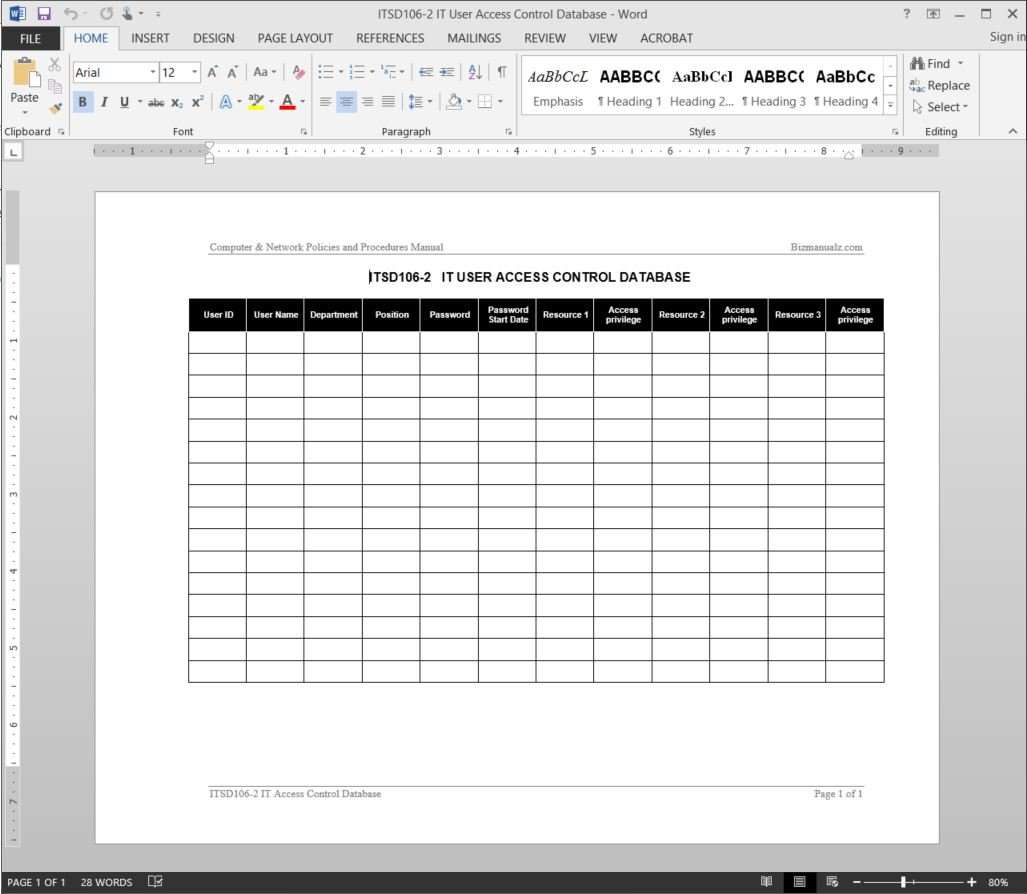
Periodic User Access Review Template

ISO 27001 Physical Asset Register Template
Enuser Access Review Policy Template
1 Create and keep an access management policy up to date Any organization must have an access management policy and you must Create a list of data and resources you need to protect Create a list of all user roles levels and access types Identify controls tools and approaches for secure access
Conducted periodically e g monthly or quarterly or during role changes a User Access Review is an essential part of your cloud security toolkit helping you create an inventory of user accounts and their privileges and verify their appropriateness based on job roles Managers or system owners often participate in the review to confirm the
Acceptable Use Policy Template TermsFeed

A Comprehensive Guide To Creating A Policy And Procedure Manual 2022

ISO27001 Risk Register Template High Table

Iso 27001 Policy Templates Free Download Resume Gallery
Guest Wireless Acceptable Use Policy Template