Web Server Uses Plain-Text Form Based Authentication - We have got Web Server Uses Plain Text Basic Authentication vulnerability in our tomcat application during our server scan We have tried enabling SSL Generating SSL certificate making changes in server xml and restarting tomcat but still this is not solving our issue Is there any solution to fix this vulnerability Thanks in Advance
Web Server Uses Plain Text Form Based Authentication Jenkins Version v1 625 3 1 When we run scan using host url we are getting this alert when we use LB URL we are getting different alerts Any suggestions will be much appreciated Thanks in advance First 2 results for LB URL scan and 3rd is HOST URL scan Scan Report tomcat jenkins Share
Web Server Uses Plain-Text Form Based Authentication
![]()
Web Server Uses Plain-Text Form Based Authentication
HTTP Plain Text Authentication Security Risks Tenable's research group recently added checks to both Nessus and the Passive Vulnerability Scanner to detect HTTP authentication which occurs over plain-text. This blog entry will discuss why this is an issue, and how the detection methods work. HTTP Plain Text Authentication Security Risks
THREAT The Web server uses plain text form based authentication A web page exists on the target host which uses an HTML login form This data is sentfrom the client to the server in plain text
Tomcat Jenkins Web Server Uses Plain Text Form Based Authentication
Unlock Jenkins To ensure Jenkins is securely set up by the administrator a password has been written to the log not sure where to find it and this file on the server C Program Files x86 Jenkins secrets initialAdminPassword Please copy the password from either location and paste it below Administrator password
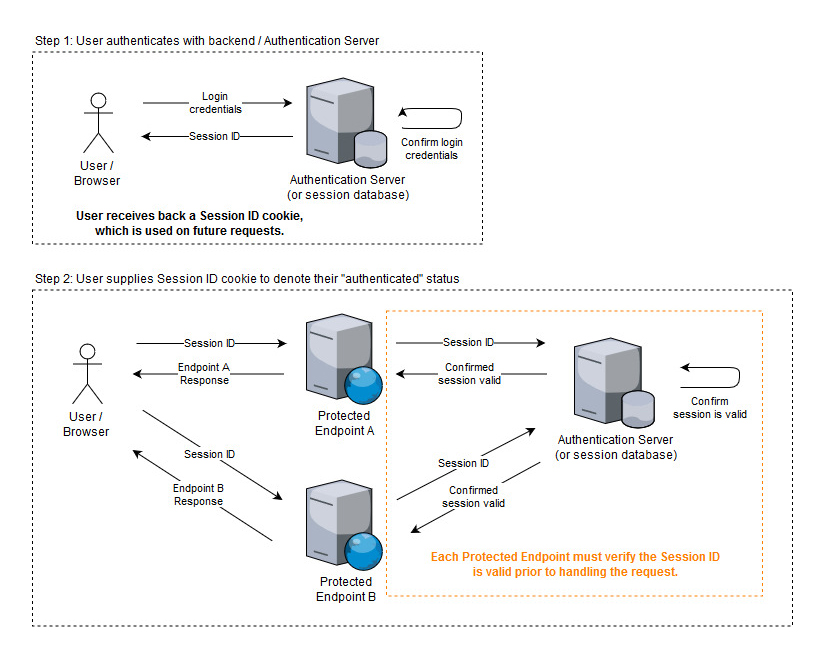
Shared Authentication With JSON Web Tokens Taylor Callsen
Security alert Web Server Uses Plain Text Form Based Authentication QID 86728 Question Qualys scanner reports vulnerability with id QID 86728 Web Server Uses Plain Text Form Based Authentication This is also known as CWE 256 How to mitigate this vulnerability Environment H series any software version Answer

Web Server Uses Plain Text Form Based Authentication UnBrick ID

Web Server Uses Plain Text Form Based Authentication UnBrick ID
Web Server Uses Plain Text Basic Authentication Vulnerability
2613023 Web Server Uses Plain Text Form Based Authentication Symptom You have ran a security scan in the AS Java and the warning in the subject has been raised
Web Servers
Web Server Uses Plain Text Form Based Authentication The Web server uses plain text form based authentication A web page exists on the target host which uses an HTML login form This data is sent from the client to the server in plain text Please let us know how to fix this We are using JIRA 5 2 11 Thanks Sujata Watch
Example 2: Form-Based Authentication Performed over HTTP. Another typical example is authentication forms which transmit user authentication credentials over HTTP. In the example below one can see HTTP being used in the action attribute of the form. It is also possible to see this issue by examining the HTTP traffic with an interception proxy.
Plaintext HTTP Authentication Detection Blog Tenable
The security vulnerability Web Server Uses Plain Text Form Based Authentication indicates that the server is transmitting unencrypted data To secure communications Transport Layer Security TLS must be enabled in the Micro Focus Directory Server MFDS and Enterprise Server Common Web Administration ESCWA 21 Sept 2023 Knowledge URL Name

DevOps SysAdmins Web Server Uses Plain Text Basic Authentication Vulnerability YouTube

Web Server Uses Plain Text Basic Authentication UnBrick ID
Web Server Uses Plain-Text Form Based Authentication
Web Server Uses Plain Text Form Based Authentication The Web server uses plain text form based authentication A web page exists on the target host which uses an HTML login form This data is sent from the client to the server in plain text Please let us know how to fix this We are using JIRA 5 2 11 Thanks Sujata Watch
Web Server Uses Plain Text Form Based Authentication Jenkins Version v1 625 3 1 When we run scan using host url we are getting this alert when we use LB URL we are getting different alerts Any suggestions will be much appreciated Thanks in advance First 2 results for LB URL scan and 3rd is HOST URL scan Scan Report tomcat jenkins Share

Basics Of Web Browser Web Server Big Data And Hadoop

Web Server Uses Plain Text Form Based Authentication UnBrick ID

Web Server Uses Plain Text Basic Authentication UnBrick ID

What Is A Web Server Definition Features Uses And More 2023

CoderJony Token Based Authentication In Web API 2 Using OWIN